Risky Bulletin Newsletter
December 04, 2024
Risky Biz News: Poland arrests former spy chief in Pegasus scandal
Written by

News Editor
This newsletter is brought to you by Push Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The Polish government has detained and forcibly taken to testify in front of a parliamentary hearing over the former government's use of the Pegasus spyware.
Piotr Pogonowski led Poland's internal security agency, the ABW, from 2016 to 2020.
Under his watch, the agency bought and used the NSO Group's Pegasus spyware to spy on opposition leaders, journalists, and prosecutors investigating government corruption.
Pogonowski previously snubbed three requests to appear in front of the Parliament commission investigating his agency and the former government's abuses.
According to Notes from Poland, this marks the first time in the country's history when a witness was forcibly compelled to appear for an inquiry.
The former ruling party—Law and Order (PiS)—has continuously denied and tried to sabotage the current Tusk government's inquiry into its use of the Pegasus spyware.
PiS officials—and Pogonowski, too—have claimed the Parliament's special commission is unconstitutional and lacks any authority. They cited the ruling of the Polish Constitutional Court, which the Parliament previously ignored due to Court being packed with PiS-appointed judges.
According to reports from local media, the former AWB head remained dismissive during the hearing and provided vague answers to most of the commission's questions.
After being elected last year, the Tusk government has made it a top priority to investigate the former government's abuses—with the Pegasus spying scandal being at the core of its efforts.
Earlier this year, Polish prosecutors charged a former PiS government official with abuse of power related to the purchase of the Pegasus spyware using ministry funds in 2017.
Officials claimed Michał Woś, a PiS member who served as undersecretary in the Ministry at the time of the purchase, diverted money from legitimate government funds to finance the Pegasus acquisition.
Just like Pogonowski, Woś denied any wrongdoing and also took the same "commission is unconstitutional" take his party took before.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
ENGlobal cyberattack: In an SEC filing on Monday, US engineering giant ENGlobal has disclosed a security breach. The company is a major contractor for the US energy sector and the federal government.
RECOPE ransomware attack: A ransomware attack has disrupted the operations of RECOPE, the largest oil refinery in Costa Rica. The company says it had to revert to manual operations and is now monitoring and refueling tankers without the help of its normal software. RECOPE imports, refines, and distributes fossil fuels across Costa Rica and neighboring countries and is the largest company in Central America. [Additional coverage in The Record]
Signzy breach: KYC service provider Signzy has suffered a security breach after the data of some customers briefly appeared on hacking forums. According to TechCrunch, the breach occurred after one of the company's employees got infected by an infostealer. The incident took place last week and Signzy said it's still investigating its ramifications. The Indian company claims to serve over 600 financial companies all over the globe.
Clipper DEX crypto-heist: A threat actor has exploited a vulnerability in the API of the Clipper DEX exchange and has stolen almost $500,000 worth of TVL crypto tokens. The stolen funds represent 6% of the total amount of TVL tokens in circulation. The company has paused all operations to investigate the attack.
XT Exchange crypto-heist: The XT cryptocurrency exchange has paused all transactions while it is investigating reports of a security breach. Threat actors are believed to have stolen around $1.7 million worth of tokens through an unknown vector. The platform claims it has more than enough reserves to reimburse affected users.
DMM Bitcoin shuts down after hack: Japanese cryptocurrency exchange DMM Bitcoin is shutting down operations in the aftermath of a major security breach earlier this year. The company was hacked for $305 million in late May and has yet to resume service. The hack is the eighth-largest crypto heist in history. DMM says it has now sold customer accounts and assets to a holding corporation. It previously guaranteed that customers would receive full reimbursement of all stolen assets. [Additional coverage in NHK]
General tech and privacy
New Apple biometrics recognition patent: Apple has filed a patent for a new type of person-detection system that uses AI and combines multiple biometrics identifiers to distinguish between individuals. Experts believe Apple will use the new patent on a rumored security camera the company is allegedly developing. [Additional coverage in 9to5Mac]
Employee sues Apple over surveillance practices: An Apple employee is suing the company over alleged monitoring of personal devices and iCloud accounts. The lawsuit alleges that Apple forces employees who use their personal devices for work to install software that tracks all their activity. The surveillance allegedly takes place even when employees are off-duty or after they have left the company. The lawsuit was filed by Amar Bhakta, an employee in Apple's advertising division since 2020. [Additional coverage in Semafor]
AWS announces physical transfer terminals: Amazon has launched AWS Data Transfer Terminal, a new feature that allows customers to upload data to the AWS cloud via a secure terminal at a physical location. Amazon says the feature was developed for customers who have a need for secure uploads or large data transfers that may take too much time over a network connection. The first two terminals are available at locations in Los Angeles and New York, with plans to add more locations next year.
FTC action against data brokers: The US Federal Trade Commission has taken regulatory actions against two US-based data brokers. The agency has banned Mobilewalla, Gravy Analytics, and its subsidiary Venntel from selling the geolocation data of their users. The FTC cracked down on the three companies after they were caught collecting and selling such information without their customers' consent. The FTC says the data contained information about military sites, churches, labor unions, and other sensitive locations. The agency specifically singled out Mobilewalla for selling geolocation data to identify women who visited pregnancy centers and individuals who attended George Floyd protests.
FTC action against IntelliVision: The FTC has barred IntelliVision from advertising AI-powered facial recognition software after the agency caught the company lying about its training methods and facial recognition capabilities.
"Furthermore, the complaint alleges that IntelliVision did not train its facial recognition software on millions of faces, as it claimed, and instead trained its technology on images of approximately 100,000 unique individuals, and then used technology to create variants of those same images. The FTC also says that IntelliVision did not have adequate evidence to support its claim that its anti-spoofing technology ensures the system can't be tricked by a photo or video image."
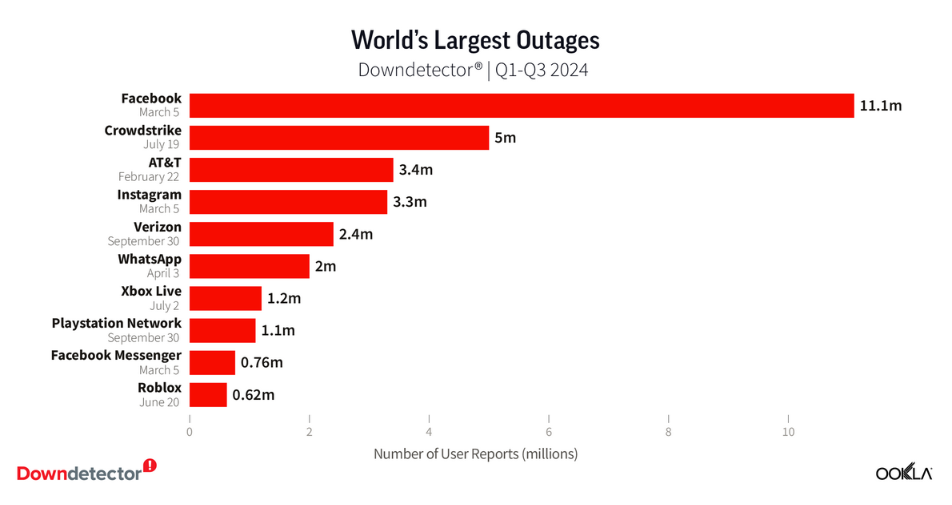
Largest outages of 2024: DownDetector has published a summary of the largest IT outages of the year. Believe it or not, CrowdStrike is not on top.
Government, politics, and policy
CFPB proposal: The US Consumer Financial Protection Bureau has proposed a new rule that would ban data brokers from selling certain types of personal and financial information of American citizens.
EU approves CSA: After more than a year of deliberations and discussions, the EU Council has finally given the green light to the EU Cyber Solidarity Act, a legislative effort to improve cybersecurity across EU member states and establish a common incident response plan. More steps to follow.
"Following their signature by the presidents of the Council and of the European Parliament, both legislative acts will be published in the EU's official journal in the coming weeks and enter into force 20 days after this publication."
Germany sets up info-ops task force: The German government has set up a special task force to detect and counter foreign disinformation and espionage campaigns targeting the country's snap election next year. The task force will work under the Federal Office for the Protection of the Constitution (BfV), the country's domestic intelligence agency. The agency says Russia has launched an information war against the West and has used disinformation, cyberattacks, and real-world sabotage to support pro-Russian and anti-EU candidates. Germany's snap election is scheduled to take place in February next year. [Additional coverage in Reuters]
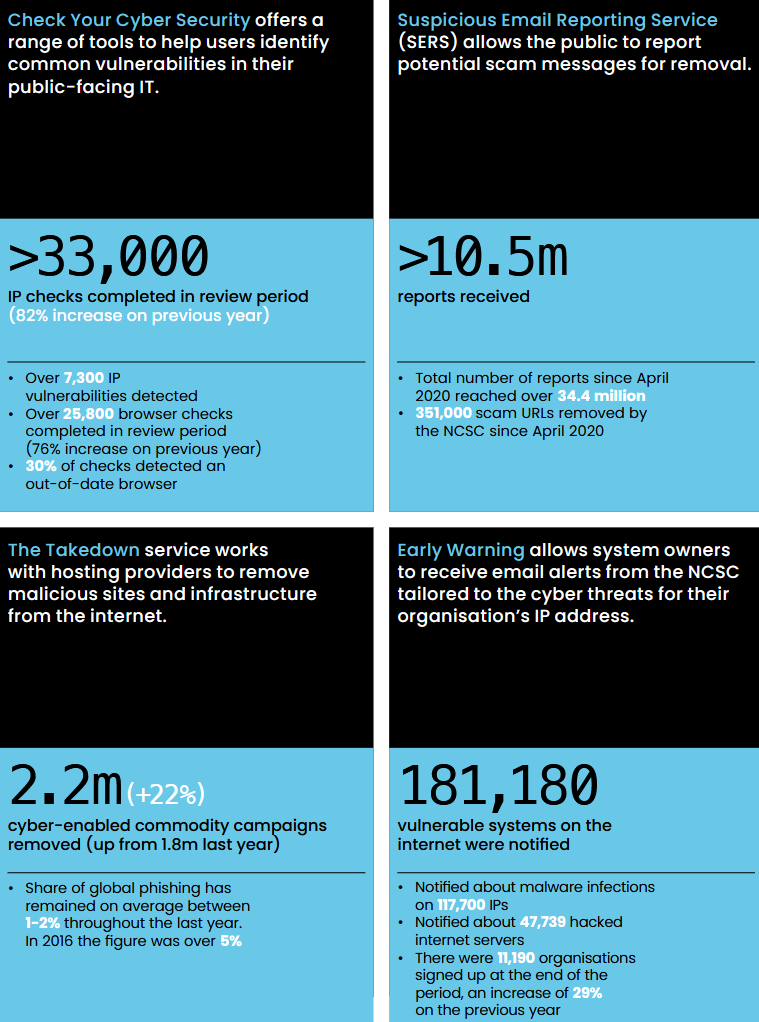
UK NCSC annual review: The UK's cybersecurity agency has taken down over 2.2 million malicious assets used in malware and phishing campaigns over the past year. The takedowns were part of Share and Defend, a new active cyber defense service that shares threat indicators with British ISPs. The UK NCSC says it also scans and notifies server owners of vulnerable systems. Over the past 12 months, the agency says it notified owners of over 180,000 unpatched systems and of almost 48,000 hacked servers. The report also concludes that most UK organizations are widely underestimating the dangers and risks from cyberattacks. [More stats in the NCSC's annual review report]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Jacques Louw, co-founder and chief product officer at Push Security, on the company's new stolen credentials detection feature, how AitM phishing can be spotted in the browser, and how Push deals with customers needing help with MFA.

If you want to get in on the ground floor of modern identity security research, Push is currently recruiting for a Security Researcher. Join their team of ex red and blue teamers leading identity attack research and creating next-gen detections in the browser. Apply here:

Arrests, cybercrime, and threat intel
Matrix takedown: Law enforcement agencies from multiple countries have taken down MATRIX, an encrypted messaging platform used by criminal groups. Authorities say they seized control of the platform earlier this year and have spent the last three months intercepting messages and gathering evidence. Officials shut off the platform and made coordinated arrests this week, on December 3. The investigation started years before after Dutch authorities discovered the MATRIX app on the phone of a criminal convicted for the murder of a Dutch journalist. The MATRIX platform should not be confused with the similarly-named Matrix open-source communications protocol.

Crimenetwork takedown: German authorities have seized Crimenetwork, the largest dark web marketplace for German-speaking users. The platform launched in 2012 and was known for the trade in stolen data, drugs, and counterfeit documents. Before it was taken down, Crimenetwork had amassed more than 100,000 users and more than 100 verified sellers. Officials say the platform made over €93 million from the sale of illegal goods and services over the past six years alone.
Hydra founder sentenced: A Moscow court has sentenced the founder of the Hydra dark web marketplace to life in prison. Officials say Stanislav Moiseyev and 15 accomplices ran the marketplace between 2015 to 2022—when it was seized by German authorities. The 15 accomplices were also sentenced and received sentences between eight years and 23 years in prison. Hydra was a major source of the drug trade across Europe and Russia. Russian officials say they seized a metric ton of narcotics after raids on the suspects' home. [Additional coverage in The Moscow Times]
DDoS suspect arrest: Japanese authorities have arrested a Chinese couple for ordering DDoS attacks against a Kyoto company that refused a business partnership. The couple ordered the attacks via WeChat and targeted the website of a Kyoto sports gym.
Crypto ATM gang detained: Russian authorities detained the members of a criminal group who installed malicious crypto ATMs across Russia and stole user funds.
DarkRaaS and CornDB: KELA does its threat intel thing and says that two hacking forum users named DarkRaaS and CornDB appear to be the same person.
Malicious ads in Poland: CERT-PL has published a report on all the various malicious ads seen on large online platforms that are targeting Polish-speaking users.
ICP-Brasil incident: There's a report that Brazilian certificate authority ICP-Brasil issued an illegal TLS certificate for the google.com domain. This might not end well for the CA. We'll keep an eye on this.
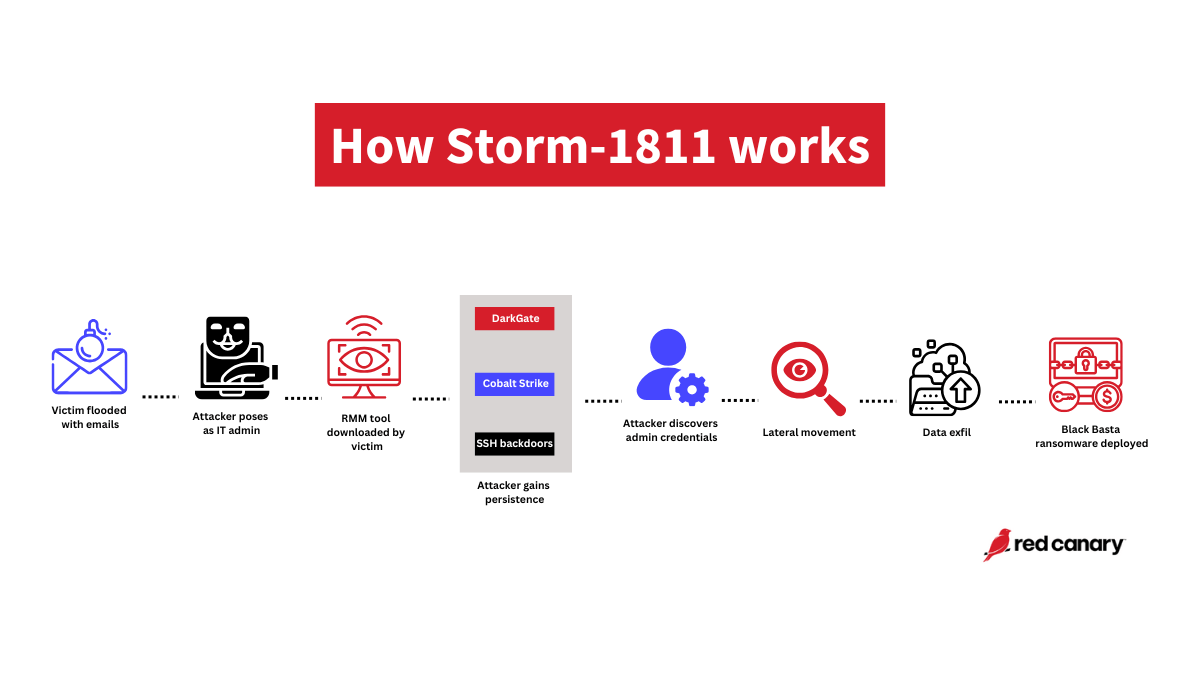
Storm-1811: Red Canary says it saw a resurgence of activity from Storm-1811, a known affiliate of the Black Basta RaaS. As before [Rapid7, Microsoft], the group relies on spam-bombing victims and then calling a company's employees, posing as their IT staff, and offering to help. The group tricks victims into installing remote access software and then stealing data and deploying the Black Basta ransomware.
Malware technical reports
Akira's Rust experiment: Check Point looks at the Akira gang's Rust-based version of its ransomware. Palo Alto Networks has also published a report on Howling Scorpius, the threat actor behind the ransomware.
Rhadamanthys Stealer: Binary Defense has published a teardown of the Rhadamanthys Stealer malware, which first surfaced in underground circles in late 2023.
Andromeda/Gamarue: Cybereason has discovered a new cluster of command and control servers for the old Andromeda/Gamarue malware—whose code had been leaked online ages ago.
Horns&Hooves campaign: Kaspersky looks at a phishing campaign they named Horns&Hooves that targets home users and business entities in Russia with payloads such as the NetSupport RAT and BurnsRAT.
Gafgyt update: Trend Micro says threat actors are now deploying the Gafgyt malware on misconfigured Docker servers. This is a change from Gafgyt's usual installbase—IoT devices. The compromised Docker servers are used for DDoS attacks.
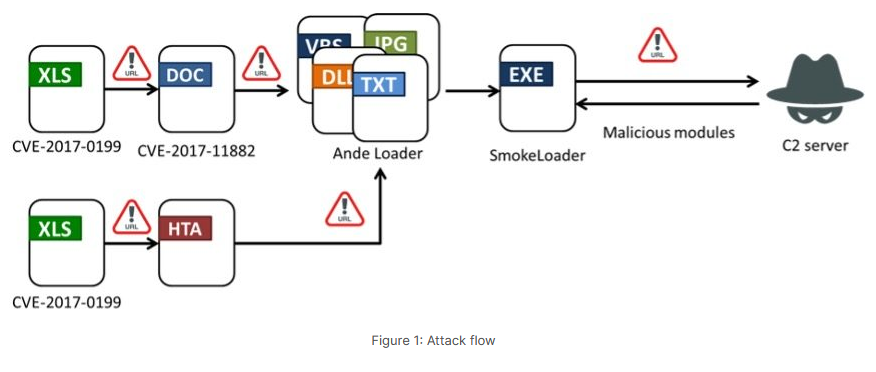
SmokeLoader: Fortinet's security team looks at a phishing campaign that targeted Taiwanese industries with the SmokeLoader malware.
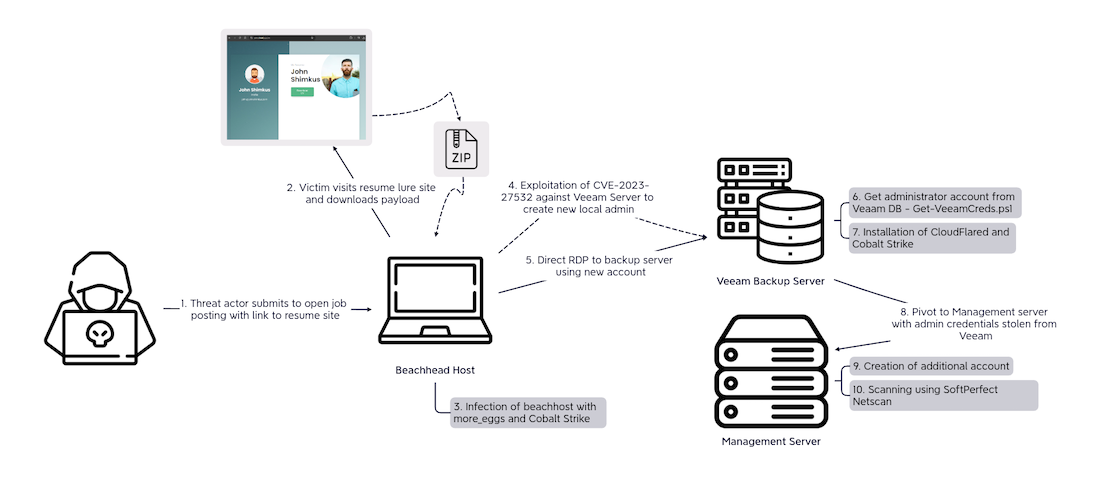
More_eggs: The spectacular DFIR Report team has published another one of their great reports—this one on the case of an infection with the More_eggs malware.
Sponsor Section
With its latest product update, Push Security takes threat intelligence feeds with stolen credentials sourced from criminal forums and compares them to the actual credentials still being used across customer environments, alerting on validated true positives only to cut through the noise.

APTs, cyber-espionage, and info-ops
APT35: ThreatBook has published a breakdown of one of APT35's fake recruitment social engineering schemes, which the Iranian group has been using to target employees in the aerospace and semiconductor sectors for the past year, compromise their systems, and then steal sensitive and proprietary information.
New Five Eyes cybersecurity guidance: Cybersecurity agencies from the Five Eyes countries have released new joint guidance on dealing with Chinese APTs targeting telco networks.
Kimsuky: South Korean security firm Genians has published a report on a recent Kimsuky spear-phishing targeting researchers investigating North Korea.
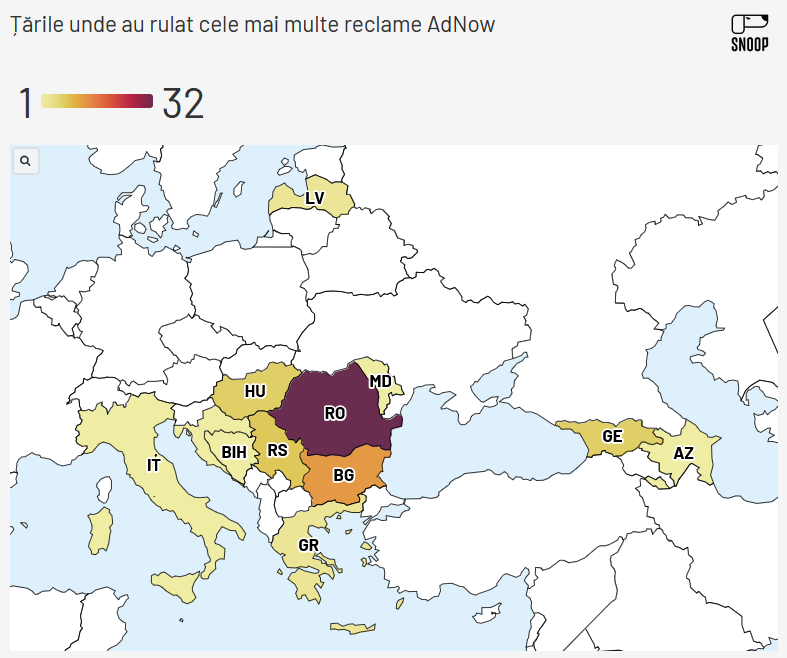
AdNow's role in info-ops: Snoop, a Romanian investigative journalism outlet, has published a report on how a Kremlin-backed ad network has secretly financed right-wing extremists and Russian propaganda through ad placement and content sponsorship deals over the past decade.
Vulnerabilities, security research, and bug bounty
2014 Cisco ASA bug under attack: Cisco says threat actors have started exploiting an old 2014 vulnerability (CVE-2014-2120) in its ASA firewalls. The vulnerability is a cross-site scripting bug in the ASA WebVPN login page. Attackers can execute malicious actions on the device just by tricking a user into clicking a link. Cisco says attacks appear to have begun last month when CISA also added the bug to its KEV database.
SonicOS RE: Security firm BishopFox has published part one of three on its reverse-engineering research of SonicWall's SonicOS firmware.
"Using our script, we were able to decrypt many variants of NSv and NSsp firmware images for analysis. This access, combined with access to other image formats we had decrypted through similar processes, allowed us to build detailed fingerprinting capabilities for SonicWall devices."
Zabbix SQLi: Qualys researchers have discovered a critical-level SQL injection vulnerability in Zabbix, an open-source software designed for monitoring IT networks. The vulnerability has received a severity score of 9.9/10 and allows remote attackers to take control of Zabbix servers via the platform's API. Zabbix released a patch for the bug (CVE-2024-42327) last week. According to Qualys, more than 83,000 Zabbix servers are exposed online and will need to be patched.
Android Security Bulletin: Google has released the Android security updates for December 2024.
KEV update: CISA has updated its KEV database with three vulnerabilities that are currently exploited in the wild. This includes the recent bugs from Zyxel, ProjectSend, and a 2023 vulnerability in the North Grid Proself client.
Veeam security updates: Backup and replication software maker Veeam has released a security update to fix eight vulnerabilities across its products.
Zyxel security updates: Taiwanese hardware vendor Zyxel has released three patches that apply to the firmware of multiple products (modems, routers, WiFi extenders, etc.).
Riot Games bug bounty rewards: Riot Games is offering $100,000 to security researchers who manage to crack Vanguard, the company's anti-cheat system. The company is also offering a similar $100,000 reward for any exploits that can also be abused to disconnect or launch DoS attacks against individual players. Riot has updated its bug bounty program after similar exploits were used to target Activision and EA games earlier in the year. [Additional coverage in PCGamer]
Infosec industry
Threat/trend reports: Interisle, the UK NCSC, and Netscout have recently published reports and summaries covering various infosec trends and industry threats.
CybersecurityDive update: Industry Dive, the parent company of CybersecurityDive, is merging with TechTarget's Informa Tech.
"Our commitment to you remains the same. Our newsroom of journalists will continue to independently report on the most notable developments, innovations and disruptions in our markets."
New tool—AtomicGen: Security researcher Burak Karaduman has released AtomicGen, a new tool for generating Atomic Red Team tests.
New tool—RequestShield: Security researcher OSINT Matter has released RequestShield, an open-source tool to analyze HTTP access.logs and identify suspicious HTTP requests and potential security threats.
New tool—KrbRelayEx: Security researcher Andrea Pierini has released KrbRelayEx, a tool designed for performing Man-in-the-Middle (MitM) attacks by relaying Kerberos AP-REQ tickets.
New tool—NativeBypassCredGuard: Security researcher Ricardo Ruiz has released NativeBypassCredGuard, a tool designed to bypass Credential Guard by patching WDigest.dll.
VirusBulletin 2024 videos: Talks from the VirusBulletin 2024 security conference, which took place in early October, are available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how the opportunities for hackers have changed and how that has altered the pipelines that turn kids into criminals.
In this podcast, Tom Uren and Patrick Gray talk about the Australian Government's extraordinary legislation that will retrospectively ensure that warrants used for the An0m crime-phone sting operation are valid.


