Risky Bulletin Newsletter
December 09, 2024
Risky Biz News: Greece is close to burying its Predatorgate scandal
Written by

News Editor
This newsletter is brought to you by Proofpoint. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
More than two years after it got caught spying on journalists and political rivals, the Greek government is still working at burying the investigation into what is now known as the Predatorgate scandal.
The incident, which rocked the Greek political scene, came to light in July 2022 when a security team of the European Parliament found traces of the Predator spyware on the phone of Nikos Androulakis, an EU MP and the president of Greece's second-largest opposition party (PASOK).
The surveillance operation was ordered by the ruling government, was conducted by the Greek national intelligence service, the EYP, and allegedly cost €7 million.
Since 2022, Greek journalists have found over 100 individuals who were targeted with malicious SMS messages that attempted to deploy the spyware.
The list included ruling and opposition politicians, ministers, local businessmen, investigative journalists, editors, the military, and even members of the EYP itself.
The ruling government tried, at one point, to claim a rogue actor was using the spyware inside Greece. Local journalists quickly shot down this theory when they unearthed documents for the spyware's purchase, but also documents showing that the EYP conducted classic surveillance operations on some of the individuals who were also targeted with the Predator spyware.
Over the past two years, the scandal was at the center of both an EU and a national investigation.
At the EU level, the now-disbanded PEGA commission found that the ruling government had indeed used the Predator spyware for both "political and economic gain."
In Greece, the government was investigated by an independent body named the Hellenic Authority for Communications Privacy and Security, or ADAE. The body concluded early on that the government used Predator illegally—since there was no explicit legal framework allowing for the spyware's deployment inside Greece's borders. That was later corrected when the government passed a law banning private individuals from using spyware but not specifically banning government bodies either.
Ever since ADAE started the investigation, the ruling government led by the New Democracy party—which was re-elected in June 2023—had constantly tried to sabotage the commission's investigation.
In September 2023, the government replaced all ADAE members hours before they were set to meet and fine the EYP for its use of the Predator spyware against civilian and political targets.
A month later, it summoned and accused the dismissed ADAE members of leaking classified information. It also blocked several attempts for ADAE to present its findings in front of the Parliament.
Earlier this month, the government tabled a bill that aims to remove key ADAE responsibilities, such as its oversight of network and communication networks and the ability to impose fines. These responsibilities are being transferred from the independent body to the government-run National Cyber Security Authority (NCSA).
If it passes, this basically sinks any ADAE investigation.
Parallel to ADAE's work, two prosecutors also started a criminal investigation against the Greek government and the EYP in late 2022. Those investigations didn't go smoother either. The Supreme Court intervened in October 2023, stripped the case from the two prosecutors, and reassigned it to someone else—which, if we are to believe the Greek press, appears to have ignored crucial witnesses and evidence.
Surprise, surprise! In August this year, the Supreme Court closed the case, citing that there was no evidence that government agencies were involved in the PredatorGate scandal.
With a re-election in its pocket and no more active investigations, the Greek government is now looking ahead. And by that we mean looking to buy new spyware.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
FBI recovers some Rain funds: The FBI has seized over $500,000 worth of crypto-assets stolen from the Rain.com cryptocurrency exchange earlier this year. The sum represents only a small fraction of the nearly $15 million that hackers stole from the exchange in late April. According to court documents, the hack took place after North Korean hackers tricked a Rain employee into infecting their system with malware while applying for a fake job on LinkedIn. The FBI says that Mandiant linked the attack to a group known as APT38 and identified the malware as a version of TraderTraitor. [Additional coverage in Forbes]
Rijeka ransomware attack: Croatian authorities say that a recent ransomware attack on the port of Rijeka did not cause any damages or disruptions to cargo operations or maritime traffic. The 8Base ransomware gang took credit for what officials described as a failed intrusion. [Additional coverage in Vecernji]
Hoboken ransomware attack: The 3AM ransomware gang has taken credit for the ransomware attack that hit the city of Hoboken, New Jersey.
Tuta DDoS attacks: Secure email provider Tuta was the targeted of a days-long DDoS attack over the last week. [Additional coverage in TechRadar]
General tech and privacy
TikTok US ban still in play: The US Court of Appeals for the District of Columbia has upheld a law that could ban TikTok in the US in January. The court rejected TikTok's argument that the ban is unconstitutional and violates the First Amendment. The court passed the ruling with a unanimous vote. TikTok says it plans to take the case to the US Supreme Court. The company sued the US government after Congress passed the law which demands the Chinese company divest its US assets or face a ban under national security concerns. [Additional coverage in the BBC/Court docs PDF]
Apple takes over crucial Firefox add-on: Apple has taken ownership of a popular Firefox browser add-on named iCloud Passwords. The add-on lets users autofill passwords from the iCloud Keychain app when signing in to websites using Firefox. The add-on's ownership was transferred over to Apple with the original developer's approval. This is now Apple's second official Firefox add-on after iCloud Bookmarks, an extension that syncs Firefox and Safari bookmarks.
Let's Encrypt to end OCSP support next year: Certificate authority Let's Encrypt says it will stop supporting OCSP on August 6, next year. Let's Encrypt announced the deprecation earlier this year when it said it was moving to CRLs. Both are technologies to allow CAs to revoke bad certificates. Let's Encrypt says it's deprecating OCSP support because of the protocol's privacy issues.
Government, politics, and policy
US lawmakers targeted in phishing campaign: A threat actor has targeted members of the US Congress with a spear-phishing campaign that urged them to download and install an encrypted messaging app. The campaign took place last week and came on the heels of an FBI security advisory that urged Americans to start using secure encrypted apps. According to NextGov, the attackers posed as an unnamed US government official. The US House Sergeant at Arms has sent a security alert to elected officials about the ongoing campaign.
US Cyber Force still on the table: The US House and Senate Armed Services Committees have agreed to carry out an independent assessment of the need to create a dedicated cyber force in the US armed forces. The assessment will be conducted by the National Academies of Sciences, Engineering, and Medicine. Earlier this year, the Pentagon tried to kill the independent assessment before it made it into the 2025 National Defense Authorization Act on Saturday. [Additional coverage in DefenseScoop]
FCC proposes new telco cyber rules: The US Federal Communications Commission has proposed new rules requiring US telcos to create and submit cybersecurity risk management plans to the agency. The proposal comes in the aftermath of a Chinese hack that breached at least US telcos over the past two years. The FCC wants to make sure telcos are keeping up with the times and investing in their cybersecurity. The agency warns that breaches at telcos can easily spread and impact other US critical sectors. [Additional coverage in CybersecurityDive]
Five Eyes warn of youth radicalization: Security agencies from the Five Eyes intelligence-sharing alliance have published a joint advisory on the radicalization of youth online and the danger it poses to national security and terrorist threats.
Roskomnadzor warns foreign web hosting companies: Russian internet watchdog Roskomnadzor issued a veiled threat over the weekend, warning that it may full-out ban eight Western web hosting companies after they failed to register with the agency. The list includes AWS, GoDaddy, DigitalOcean, Hetzner, HostGator, Kamatera, Ionos, and Network Solutions. [Additional coverage in Interfax]
Roskomnadzor tests Dagestan blockade: The Roskomnadzor has blocked access to YouTube, WhatsApp, and Telegram over the weekend in three Muslim-predominant regions—Chechnya, Dagestan, and Ingushetia. The blockade was part of a test as religious and anti-Kremlin sentiment continues to grow in the region.
Hungary spies on EU officials: A Politico report claims the Hungarian intelligence agency spied on EU anti-fraud officials visiting the country. For now, the article mentions only tapped phones and physical surveillance. No spyware was mentioned so far, but don't rule it out, since Hungary is a known Pegasus customer.
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Proofpoint senior threat intelligence analyst Selena Larson about the rise of Attacker-in-the-Middle phishing and ClickFix social engineering campaigns.
Arrests, cybercrime, and threat intel
Nigerian BEC scammer sent to prison: US authorities have sentenced a 39-year-old Nigerian national to eight years in prison for his role in a sprawling BEC operation. Okechuckwu Valentine Osuji is believed to have made at least $6 million from both BEC and romance scams. He was arrested in Malaysia and extradited to the US in 2022.
Nebraska cryptominer pleads guilty: A Nebraska man has pleaded guilty to running a large-scale illegal cryptomining operation. Officials say Charles O. Parks III used $3.5 million worth of cloud computing resources to mine over $1 million in crypto tokens. Parks rented servers from two cloud providers through fake companies and never paid his bills. Officials say he used the ill-gotten funds to buy NFTs, luxury cars, jewelry, and expensive hotels and travel. He also structured money movements to avoid reporting requirements under US laws.
Phishing gang members arrested: Belgian and Dutch police have arrested eight suspects believed to be part of an international phishing group. Officials say the gang was behind large-scale phishing campaigns that tried to get into people's banking accounts. The group posed as police or banks and even approached some of their victims at their homes. Police say the gang made victims across ten European countries, with damages estimated in the realm of millions of euros.
Ultralytics supply chain attack: A threat actor has added a hidden cryptominer into the Python package of the Ultralytics AI toolkit. The malicious version was made available through the official PyPI portal and was live for less than 24 hours. The source of the hijack has not been identified, but developers believe it may be an exploit that targeted the project's build environment.
Cobalt Strike abuse: The most recent version of the Cobalt Strike red-teaming tool has been observed being abused in the wild for what appears to be malicious activity. Security firm Hunt.io says it discovered a cluster of IP addresses running a version of Cobalt Strike 4.10, released in June this year. The company says the servers share the same fingerprint and impersonate well-known brands, suggesting they might be used in phishing campaigns. Cobalt Strike is a popular tool abused by threat actors, but most attacks take place using old, cracked versions of the software.
Rise in AitM phishing: In a blog post from November that we missed, Microsoft said it observed a 146% rise in AitM phishing attacks over the past year.
New npm malware: Fifty-three malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
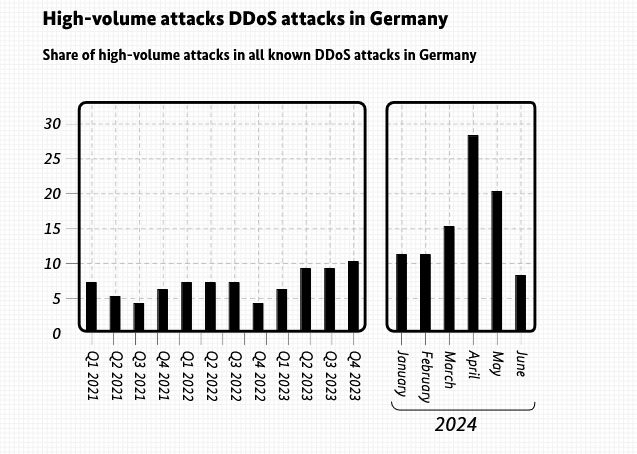
BSI says DDoS attacks were notable last year: Germany's cybersecurity agency says it noticed a dramatic increase in DDoS attacks that targeted the country over the past year. In its yearly IT security assessment report, the agency says there was a noticeable increase in high-volume DDoS attacks. The BSI says this trend suggests threat actors are now in command of large botnets that can carry out devastating attacks.
Malware technical reports
Meeten app delivers Realst infostealer: Cado security has discovered a malicious clone of the Meetio app—named Meeten—that is used in social engineering campaigns designed to infect users with the Realst infostealer.
SpyNote: CyFirma researchers have published an analysis of the SpyNote RAT, which they believe was used in a recent cyber-espionage campaign across South Asia.
CryptBot evolution: OALABS has published a technical deep dive of all the changes in CryptBot stealer versions.
Sponsor section
The Proofpoint Voice of the CISO report is drawn from a survey of 1,600 chief information security officers across 16 countries, exploring key challenges, expectations, and priorities. What does the data reveal?
APTs, cyber-espionage, and info-ops
Patchwork: Anheng Hunting Labs has published a report on recent Patchwork APT campaigns targeting government agencies and research institutes with R&D-related lures.
Doppelganger: Apparently, Namecheap is doing such a poor job at detecting info-ops, it is being called out by Correctiv's Max Bernhard for still hosting Doppelganger content.
Wagner disinformation agent interview: Forbidden Stories, Le Monde, and Spiegel have published interviews with a former Wagner employee who worked on Russia's disinformation campaigns in the Central African Republic.
More on AdNow: Intelligence Online builds on a Snoop report from last week on how Russia used an online advertising network named AdNow to pay for its propaganda and propagandists in the West and how Romania, specifically, was used as a testing ground for this strategy.
TikTok disinfo targeting Ukraine mobilization: Journalists from Ukrainian news outlet Texty have found a Russian disinformation campaign consisting of over 2,000 TikTok accounts involved in an attempt to discredit and sabotage Ukraine's mobilization campaign. The cluster was active throughout July and was extremely productive. The accounts posted over 41,000 posts that garnered over 10 million views since. Most of their activity took place over the #it'snotmyukraine hashtag. The accounts used the same avatars, channel names, and identical descriptions. Texty claims the accounts were managed by an entity that also advertises online casinos in Russia.

Vulnerabilities, security research, and bug bounty
NTLM zero-day: ACROS security researchers have discovered a new vulnerability that allows threat actors to steal NTLM credentials after a user views a malicious file in Windows Explorer. The vulnerability impacts all Windows versions, going back to Windows 7 and Windows Server 2008. ACROS has reported the bug to Microsoft and has issued its own set of micro-patches for affected operating systems.
QNAP security updates: Taiwanese equipment vendor QNAP has released security updates to patch 10 security flaws. Many of the patches were for products exploited during a recent Pwn2Own hacking contest.
SailPoint security update: Identity service provider SailPoint has patched an improper access control vulnerability (CVE-2024-10905) in its IdentityIQ platform. No details are available, but the bug is apparently a CVSSv3 10/10 bug.
ASUS security update: Taiwanese hardware vendor ASUS has released a security update for some of its RT-AX routers.
TeamCity security updates: JetBrains has released 13 patches for its TeamCity platform. No info on what exactly they fix. [h/t ScreamingGoat]
Mongoose vulnerabilities: Nozomi researchers have discovered 10 vulnerabilities in the Mongoose open-source networking library. All vulnerabilities can be exploited by sending malicious-crafted TLS packets to devices running the library. Most of the vulnerabilities can be used to crash devices or cause continuous reboots. While the vendor released a security patch, the vulnerabilities are likely to linger for years to come because the library is commonly used with IoT and industrial gear that don't receive timely updates.
DaMAgeCard attack: Security firm Positive Technologies has developed a new attack that exploits the SD Express standard to gain access to a device's memory through its SD card reader. Named DaMAgeCard, the attack exploits the fact that the new SD Express standard can operate in both SDIO mode and as a PCIe/NVMe device, allowing direct memory access. Researchers say this access can be abused via malicious custom-built SD Express cards plugged into a target device. The only attack's upside is the relatively low adoption of the SD Express standard.
Infosec industry
Brian Krebs profile: The Wall Street Journal has a very good profile on Brian Krebs, an infosec reporter who built a reputation for tracking down and doxing some of today's hackers.
Threat/trend reports: The BSI, Flashpoint, Kaspersky, Moonlock, Snyk, VulnCheck, Wordfence, and Zscaler have recently published reports and summaries covering various infosec trends and industry threats.
MSSN CTRL 2024 videos: Talks from the MSSN CTRL 2024 security conference, which took place in early October, are available on YouTube.
New tool—BootExecuteEDR: Security researcher Rad has released BootExecuteEDR, a tool to disable EDR products using local native applications.
New tool—CRXaminer: Security engineer Mark El-Khoury has released CRXaminer, a tool to examine Chrome extensions for security issues. Also hosted online here.
New tool—Malimite: Security researcher LaurieWired has released Malimite, an iOS decompiler designed to help researchers analyze and decode IPA files.
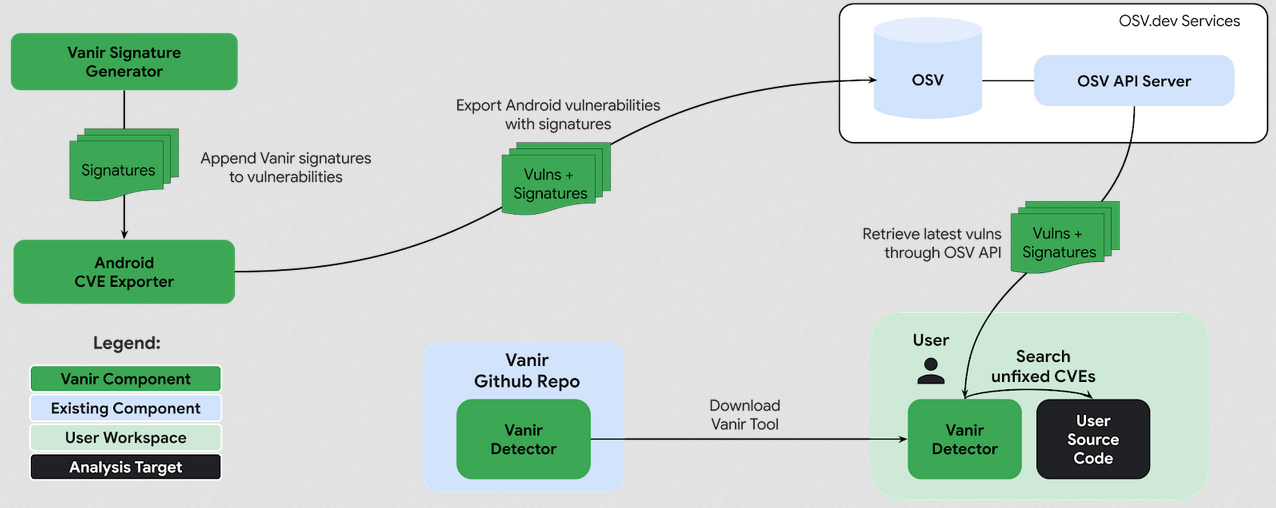
New tool—Vanir: Google has released Vanir, a tool for Android developers that scans their Android OS version and tells them what security patches they're missing.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how the opportunities for hackers have changed and how that has altered the pipelines that turn kids into criminals.
In this podcast, Tom Uren and Adam Boileau talk about the continued importance of hack and leak operations. They didn't really affect the recent US presidential election, but they are still a powerful tool for vested interests to influence public policy.
