Risky Bulletin Newsletter
December 06, 2024
Risky Biz News: Declassified documents reveal Russia's election info-ops in Romania
Written by

News Editor
This newsletter is brought to you by Push Security. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
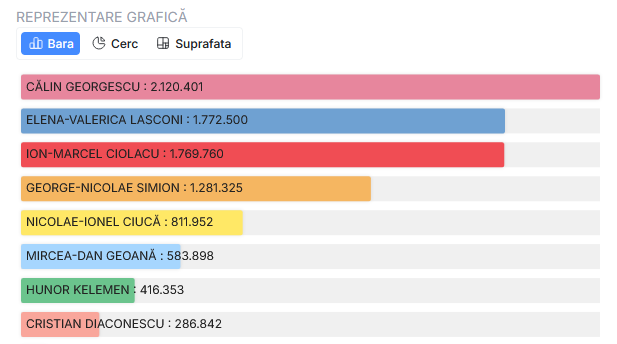
Romania's national security council (CSAT) has declassified two documents this week that reveal a coordinated propaganda campaign that boosted an obscure far-right and pro-Kremlin candidate into the country's first round of presidential elections.
The campaign, which mostly took place via TikTok, took Calin Georgescu from an unknown candidate who was only polling around 1% a month before the election to the winner of the first presidential election round, where he accounted for almost a quarter of all votes.
The documents did not formally attribute the operation, but in a subsequent statement this week, the US State Department said what every Romanian politician and regular citizen already said and knew—that this was Russia.
The first of the two documents [PDF] covers a huge TikTok campaign that pushed messages in support of Georgescu, while a second document [PDF] describes cyberattacks that targeted Romania's election infrastructure on the first Presidential election leg, on November 24.
According to Romanian intelligence services (SRI), Georgescu's sudden rise in popularity was primarily backed by more than 25,000 TikTok accounts registered years before that came to life two weeks before the election.
TikTok, which cooperated with Romanian authorities for the investigation, said the accounts were managed through "unique" IP addresses, which allowed the network to go undetected by the company's coordinated behavior detection systems.
The Chinese social media company says the bot accounts posted videos of Georgescu or his messaging, and also commented on his posts to boost their visibility.
The bots used the same hashtags and strings of emojis designed to exploit TikTok's algorithms and boost their content. They also used videos of famous Romanian athletes and government bodies to suggest Georgescu was a broadly supported and popular figure. In reality, Google searches for Calin Georgescu's name spiked after the election because most Romanians had no clue who he was.
Human-operated accounts were also involved. According to the SRI and Romanian media, Telegram channels and groups were involved in a scheme to pay anyone who boosted Georgescu-themed content. According to Moldavian reporter Paula Erizanu, the same tactics Russia used in the recent Moldovan presidential election were also used in Romania.
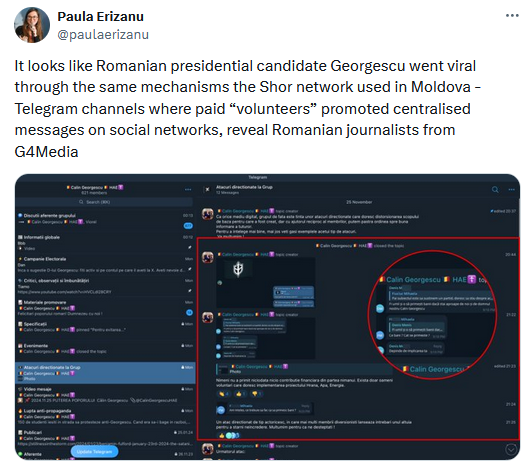
This type of pay-to-promote scheme was also coordinated through a TikTok account named @propagatorcg, which provided instructions and paid users to propagate Georgescu's content on TikTok, YouTube, and Facebook.
Citing TikTok data, the SRI says that a Romanian businessman named Bogdan Peșchir, who operated the @BogPR TikTok account, also paid at least €381,000 to TikTok users to promote Georgescu's content.
The declassified document mentions that several Romanian social media influencers received money to promote Georgescu's candidate—with several influencers already admitting to local media.
TikTok says it suspended two activity clusters linked to this campaign, including one that appears to have had ties to Russian news agency Sputnik.
From the declassified documents, Romanian officials are pretty angry at TikTok for several reasons. The company failed to detect the propaganda accounts in time, failed to mark the Georgescu-themed posts as politically themed, and then refused to remove the content—only blocking it for Romania-based users but leaving it available to international audiences and the Romanian diaspora. Officials say this not only broke Romanian election laws but the company's own policies.
The Romanian security council says that while other Romanian political candidates labeled their TikTok content properly and saw a fraction of the coverage, Georgescu's obvious political posts were trending among Romanian audiences, and the company never intervened.
There's a palpable smoldering anger towards TikTok from the Romanian political class and a huge chunk of the Romanian audience.
In the days after the first presidential election round, Romania's media watchdog floated the idea of blocking access to TikTok across the country. The agency had a change of heart the next day, but Romanian officials still filed a report against TikTok with EU authorities.
A week later, the European Commission issued a what appears to be its first retention order under the EU DSA, demanding that TikTok preserve any data and accounts linked to the Romanian elections.
On December 5, Romanian prosecutors opened a formal investigation into the Georgescu camp for money laundering and breaking election laws. The investigation stems from one of Georgescu's claims that he spent zero Romanian lei to finance his campaign.
As for the second document, the SRI says that while some attempts were made to access and disrupt official election websites and infrastructure, none had any impact. The only successful break-in impacted a GIS mapping server linked to the electoral registry.
Romania's second presidential election round is scheduled for this weekend, December 8. The round is expected to break attendance records after the Parliament elections last weekend—where the pro-EU and pro-NATO camp barely edged a victory—had a massive turnout not seen in decades.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Stoli files for bankruptcy after ransomware attack: The American division of vodka maker Stoli has filed for bankruptcy in a Texas court last week. Stoli cited a ransomware attack in August and the seizure of its assets in Russia as the main issues that impacted its operations. The company said recovery from the ransomware attack would not have been possible before March next year. Stoli also lost access to its ERP platform, which severely impacted its ability to control key processes, such as supply, production, and order deliveries. The company also cited huge losses after its Russian assets were seized by authorities after the country's invasion of Ukraine. [Additional coverage in CNN]
BT ransomware attack: The Black Basta ransomware gang has successfully breached the business division of the BT Group, formerly known as British Telecom. The company said the attack had no impact on its services or the BT Conferencing platform, which the group seems to have hit. [Additional coverage in BleepingComputer]
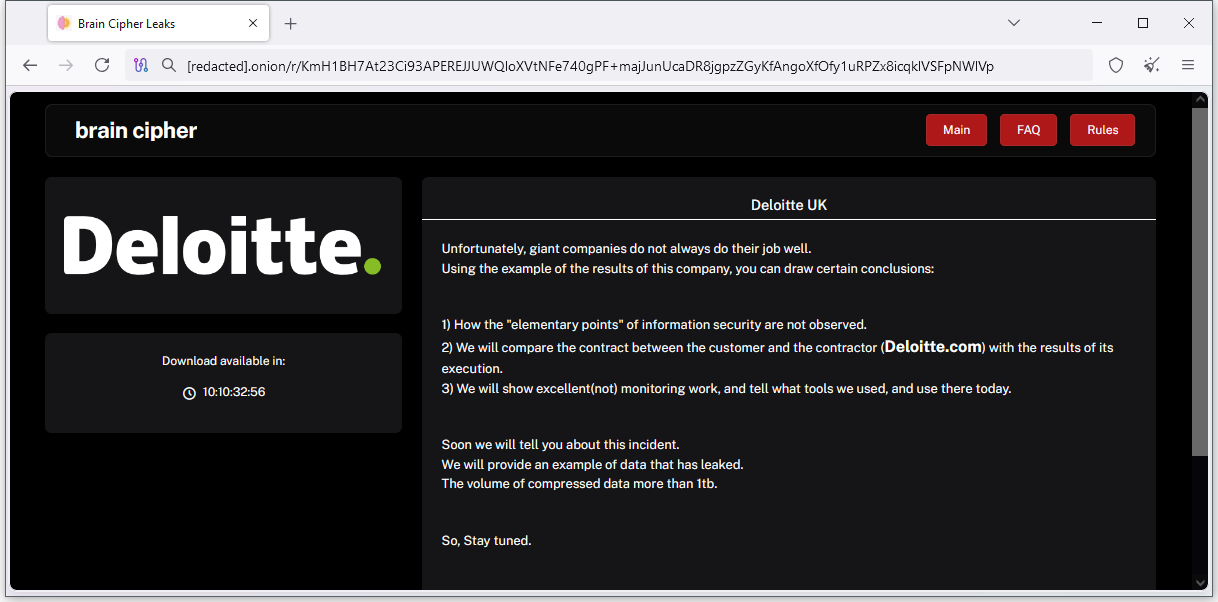
Deloitte ransomware attack: The Brain Cipher ransomware gang claims it hacked auditing and consulting giant Deloitte. The company has not confirmed.
Gazprombank DDoS attacks: Ukraine's military intelligence agency GUR says it conducted DDoS attacks against Russia's Gazprombank. [Additional coverage in the Kyiv Independent]
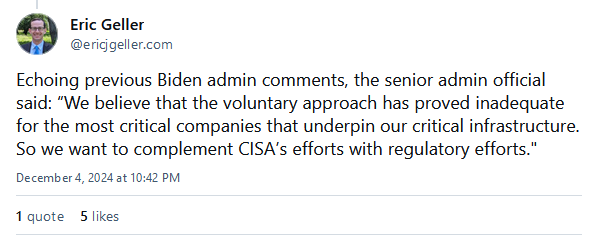
Salt Typhoon hack update: The White House says that at least eight US telcos have been hacked by a Chinese hacking group known as Salt Typhoon. Deputy National Security Adviser for Cyber Anne Neuberger says the hacks have been underway for likely one or two years and have also hit dozens of other countries. Neuberger says the hackers accessed a large quantity of metadata while hunting for the calls and texts of specific targets. A day before, the FBI said the intrusions were still ongoing, and they were still fighting to evict Salt Typhoon from the compromised networks. CISA Director Easterly says the CSRB investigation into the Salt Typhoon hacks is set to launch this week on Friday.
General tech and privacy
TPM requirement stays: With the Windows 10 EOL approaching next year in October, Microsoft says it won't budge on having the TPM requirement for migrating to Windows 11. Devices without support for the TPM 2.0 standard will not be able to install Windows 11, which means loads of old devices will remain on Windows 11 or need to switch to some other OS like Linux.
"In conclusion, TPM 2.0 is not just a recommendation—it's a necessity for maintaining a secure and future-proof IT environment with Windows 11. And it's an important part of the larger Zero Trust strategy, alongside Secure Boot, Credential Guard, and Windows Hello for Business."
Mozilla rebrand: Mozilla has updated its corporate identity with a new logo.

Government, politics, and policy
Iranian hackers target FBI director pick: Iranian state-sponsored hackers are believed to have accessed the communications of Kash Patel, Donald Trump's nomination for the post of FBI Director. According to Semafor, the hack hit multiple other members of the Trump transition team. This marks the second time Iranian hackers have breached the Trump camp this year after breaching his campaign staff in June.
NATO statement: NATO Secretary General Mark Rutte says Russia and China are trying to destabilize NATO members using acts of sabotage and cyberattacks.
Free cyber assessments: The US state of Indiana, through a special program, will provide free cybersecurity assessments to local water and wastewater facilities. [Additional coverage in StateScoop]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Jacques Louw, co-founder and chief product officer at Push Security, on the company's new stolen credentials detection feature, how AitM phishing can be spotted in the browser, and how Push deals with customers needing help with MFA.

Arrests, cybercrime, and threat intel
New Scattered Spider arrest: US authorities have arrested and indicted a California teen suspected of being a member of the Scattered Spider hacking group. US officials claim that Remington Ogletree hacked two telcos and sent millions of phishing links via SMS in an attempt to hack and steal cryptocurrency. Ogletree is the sixth member of the group that was charged in the US over the past month. According to Bloomberg, he was detained and later released on a $50,000 bail last month.
ShinyHunters member charged in France: French authorities have charged a member of the ShinyHunters hacking group with selling malware designed to hack AWS email servers. According to Le Monde, Sébastien Raoult created software that could scan and hijack vulnerable SMTP servers running on AWS cloud infrastructure. He allegedly sold the software online between 2021 and 2022. Raoult is a famous hacker known as Sezyo Kaizen, one of the three members of the ShinyHunters group. He was sentenced to three years in a US prison in January this year. According to ParisMatch, Raoult was extradited back to France this week at the request of French authorities to face the new charges. [h/t Gabriel Thierry]
NCA disrupts Russian money laundering networks: UK authorities have disrupted two money laundering networks used by drug cartels, ransomware, and Russian espionage operations. Officials have arrested 84 individuals linked to Smart and TGR, the two companies at the heart of the laundering operations. Smart and TGR allegedly laundered billions of US dollars via cryptocurrencies and networks of front companies. The US Treasury Department has sanctioned six Smart and TGR executives, including their main administrators—identified as Ukrainian national George Rossi and Russian national Ekaterina Zhdanova. Zhdanova had been on the Treasury sanctions list since last year for her role in laundering Ryuk ransomware payments.

Manson Market takedown: Europol has taken down Manson Market, a cybercrime platform that sold stolen personal and financial information. Two suspects were arrested in Austria and Germany, and more than 50 servers were seized across Europe. Officials say cybercrime groups and online scammers used the Manson Market to sell data they extracted from their victims. Tactics included using fake online stores to collect data through payment forms or by calling users and posing as bank employees.
Electric Ireland arrest: Irish police have detained a woman for her alleged role in a breach of energy provider Electric Ireland at the end of last year, per the Irish Times.
DocuSign phishing: Cado Security and Perception Point warn about new waves of DocuSign phishing currently going on.
Cloudflare abuse: Fortra has seen an increase in abuse of Cloudflare's pages[.]dev and workers[.]dev domains for phishing operations.
Cybercrime Black Friday deals: Bitdefender has published a report looking at the Black Friday and Cyber Monday "deals" that popped up on cybercrime forums.
DDoS campaigns in Australia: Radware has published a report on a recent wave of over 60 DDoS attacks that targeted Australian organizations and were conducted by pro-Kremlin and pro-Palestinian groups.
PARANODEUS: CyFirma researchers have published a report that looks at various malware offerings from a threat actor named PARANODEUS. The package includes an infostealer, ransomware, and a screen locker.
New Pegasus infections: Security firm iVerify says it found seven devices infected with the Pegasus spyware among its userbase after customers used an optional spyware-scanning tool it developed earlier this year.
Solana supply-chain attack: A threat actor has added malicious code to the official JavaScript SDK of the Solana cryptocurrency project. The malicious code was designed to steal private keys from apps where the SDK was used and then drain user accounts. The Solana project blamed the incident on a compromised developer account.
The Com & 764 LEA alert: According to CyberScoop, law enforcement agencies are circulating private alerts about online groups like The Com, 764, MKU, and others, which are now using cybercrime-specific tactics and tools to harass, dox, and carry out violent attacks against adults and children across the US.
Malware technical reports
DroidBot: Cleafy researchers have discovered a new Android banking trojan named DroidBot. Cleafy says the malware is offered through a MaaS and appears to be the work of Turkish-speaking devs.
Black Basta resurgence: Rapid7 notes a resurgence in Black Basta social engineering campaigns, most likely what Red Canary saw in their Storm-1811 report earlier this week.
RedLine: Kaspersky looks at cracks and activators for business software spreading on Russian forums that are laced with the RedLine infostealer.
RevC2 and Venom Loader: Zscaler researchers have published a report on RevC2 and Venom Loader, two new malware strains used by the Venom Spider (GOLDEN CHICKENS) cybercrime group.
Sponsor Section
With its latest product update, Push Security takes threat intelligence feeds with stolen credentials sourced from criminal forums and compares them to the actual credentials still being used across customer environments, alerting on validated true positives only to cut through the noise.

APTs, cyber-espionage, and info-ops
Chinese APT abuses VSC for C2: A Chinese cyber-espionage group is abusing Visual Studio Code and Microsoft Azure infrastructure for command-and-control (C2) purposes. According to SentinelOne, this is the first APT the company has seen abusing Visual Studio Code for C2 purposes. SentinelOne says the group also used lateral movement techniques it believes were acquired from a shared vendor or a digital quartermaster providing shared tooling for the Chinese APT ecosystem.
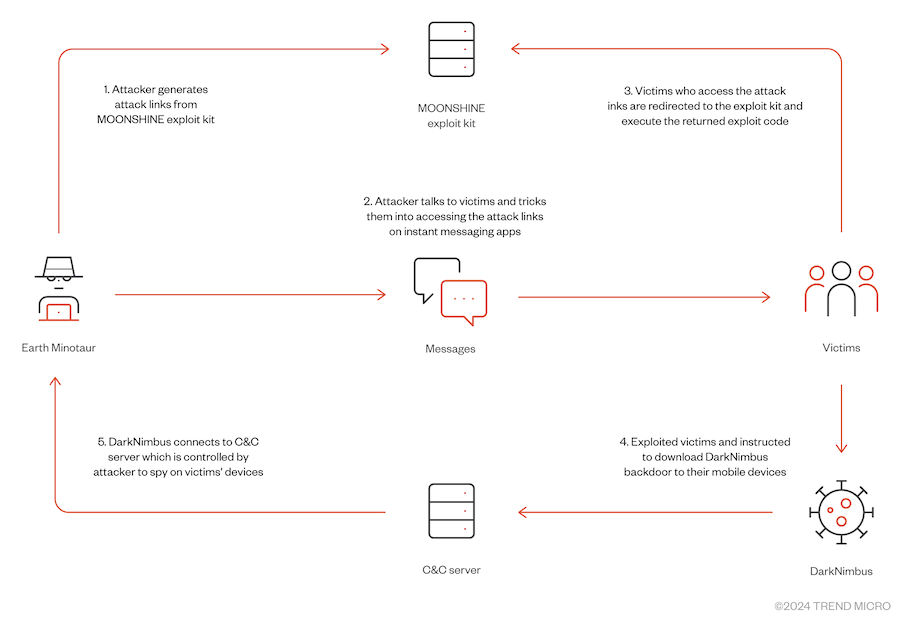
Earth Minotaur: Trend Micro looks at the hacking tools of a Chinese APT group named Earth Minotaur that has historically targeted Uyghur and Tibetan minorities. The report covers tools such as the Moonshine exploit kit and the DarkNimbus Android and Windows backdoor. Trend Micro says it identified 55 Moonshine exploit kit servers in the wild, many still active.
Chinese espionage campaign: Broadcom's Symantec has published a report about an unnamed Chinese APT group's attack on a US company with a large presence in China. No official attribution, but Symantec says the tooling has obvious links to past Chinese attacks.
"While it is possible that actual network intrusion occurred earlier, the first evidence of the attacker's activity dates from April 2024, and this malicious activity continued until August 2024."
Sichuan Silence profile: The Natto Thoughts team has published a profile on Sichuan Silence, a Chinese IT firm that provides vulnerability research and hacking tools to the Chinese government—and the company that was developing the exploits and backdoors deployed on Sophos firewalls as part of the Pacific Rim campaign. According to an older Meta report, the company was also involved in social media info-ops, so quite the versatile capabilities.
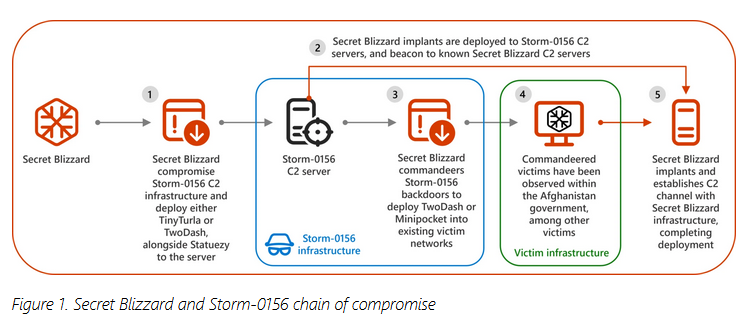
Turla hacked Pakistani APT infrastructure: A Russian cyber-espionage group has hijacked the infrastructure of a Pakistani APT group and used it to launch its own attacks for at least the past two years. Researchers at Lumen and Microsoft say Turla operators hacked the command and control servers of Pakistan's Transparent Tribe at the end of 2022. The group used the servers to push its own payloads to victims previously infected by Transparent Tribe. Microsoft says Turla has hacked at least six other APTs over the past seven years. The only previous public case is Iranian APT group OilRig in 2019.
FSB deploys spyware on detained suspect's phone: Russia's FSB intelligence agency secretly installed spyware on the device of an ethnic Ukrainian programmer. The spyware was installed on his phone after officials arrested Kirill Parubets in April this year on charges of sending money to Ukraine. He was forced to unlock his phone while under arrest under the threat of being charged with treason and murder. Parubets later found the spyware after being set free after 15 days. According to a joint technical investigation from Citizen Lab and First Department, the device was infected with a version of Monokle, a mobile spyware strain developed by a known Russian government contractor named the Special Technology Center. Parubets and his wife fled the country shortly after the incident.
APT-C-53 (Gamaredon): Qihoo has published a report on APT-C-53's recent phishing campaigns. The APT is also known as Armageddon or Gamaredon and operates out of Crimea.
BlueAlpha (Gamaredon): Recorded Future has also published a report on the same group's abuse of Cloudflare Tunnels for staging malware during its phishing campaigns. Obviously, the campaigns target Ukrainian organizations.
New Doppelganger operator: Meta's security team has identified a third Russian organization that is behind a sprawling influence operation known as Doppelganger. The social media giant says it tracked recent Doppelganger activity to individuals associated with the Moscow State Institute of International Relations (MGIMO). Previously, Meta linked Doppelganger activity to two Russian companies named Structura and the Social Design Agency, both of which have been sanctioned by the US and the EU. [Additional coverage in Meta's Q3 Adversarial Threat Report/PDF]
Vulnerabilities, security research, and bug bounty
I-O DATA zero-days: Threat actors are exploiting three zero-days in the routers of Japanese hardware maker I-O DATA. The zero-days include a bug that can allow hackers to modify sensitive settings, run OS commands, and disable the router's firewall. I-O DATA says it received reports of abuse in the wild from customers in mid-November. The company has already released a fix for one of the zero-days, and fixes for the other two are scheduled for December 18.
CyberPanel exploitation: CISA says threat actors are exploiting a second vulnerability in the CyberPanel web hosting system. The first was CVE-2024-51567, but CISA says threat actors are now exploiting CVE-2024-51378 as well. The two vulnerabilities are believed to have been used to deploy the PSAUX ransomware on unpatched systems.
Veeam exploitation: Arctic Wolf says that a Veeam RCE patched earlier this week—CVE-2024-42448—is now under active exploitation. The vulnerability allows threat actors to execute remote code on Veeam Service Provider Console servers. VSPC servers are used in enterprise environments to manage and monitor Veeam backup agents.
New Mitel MiCollab unauth path traversal: watchTowr researchers have identified a new unauthenticated path traversal vulnerability in the Mitel MiCollab VoIP platform. Researchers say they found CVE-2024-41713 while analyzing a recent MiCollab n-day tracked as CVE-2024-35286. The path traversal was patched in October and watchTowr has now released details and a PoC.
Lorex camera vulnerabilities: Rapid7 researchers have identified and helped patch five vulnerabilities in Lorex indoor security cameras.
"The exploit chain consists of five distinct vulnerabilities, which operate together in two phases to achieve unauthenticated RCE. Phase 1 performs an authentication bypass, allowing a remote unauthenticated attacker to reset the device's admin password to a password of the attacker's choosing. Phase 2 achieves remote code execution by leveraging the auth bypass in phase 1 to perform an authenticated stack-based buffer overflow and execute an operating system (OS) command with root privileges. [...] The five vulnerabilities are listed below."
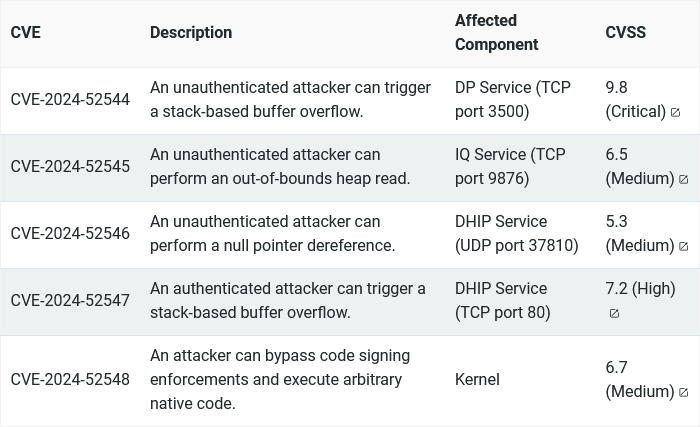
Cisco security update: Cisco has released a security update for NX-OS to fix a firmware image verification bypass found by Google Cloud researchers.
SolarWinds security update: SolarWinds has released a fix for its main platform to fix an XSS bug.
SonicWall security update: SonicWall has released a security update for its SMA SSL-VPN appliance to fix six vulnerabilities.
SafeMarshal escape: Security researcher Luke Jahnke has published an escape for SafeMarshal, a new Ruby security gem that can be used to block deserialization attacks.
Browser isolation bypass: Mandiant has published details about a novel technique its researchers developed to bypass three types of browser isolation methods.
"In this blog post, Mandiant demonstrated a novel technique to establish C2 when faced with browser isolation. While this technique proves that browser isolation technologies have weaknesses, Mandiant still recommends browser isolation as a strong protection measure against other types of attacks (e.g., client-side browser exploitation, phishing, etc)."
WAF bypass via cookies: PortSwigger's Zakhar Fedotkin has published research on how threat actors can bypass WAFs using the $Version attribute in cookie header files.
AI slop impact on project maintainers: Seth Larson, the maintainer of several crucial Python projects, says he is seeing an increase in "extremely low-quality" security reports submitted by bug hunters, suggesting researchers are using AI/LLM tools to discover vulnerabilities and put together reports.
"If this is happening to a handful of projects that I have visibility for, then I suspect that this is happening on a large scale to open source projects. This is a very concerning trend. [...] Security reports that waste maintainers' time result in confusion, stress, frustration, and to top it off a sense of isolation due to the secretive nature of security reports. All of these feelings can add to burn-out of likely highly-trusted contributors to open source projects. In many ways, these low-quality reports should be treated as if they are malicious."
Infosec industry
Threat/trend reports: Gen Digital, Genetec, KnowBe4, the Linux Foundation, and Orange have recently published reports and summaries covering various infosec trends and industry threats.
New tool—Library of Leaks: DDoSecrets has released Library of Leaks, an online database of millions of hacked and leaked documents.
New tool—Deck.Blue: Software engineer Gildásio Filho has released Deck.Blue, a TweetDeck-like platform for BlueSky.
New tool—Cyd: Micah Lee has released Cyd, a revamped version of Semiphemeral that can back up and delete all your tweets. Another similar tool is Redact, which we featured in an edition last month.
New tool—hrtng: Kaspersky has open-sourced hrtng, its internal IDA Pro plugin used for various malware reverse-engineering tasks.
BSides Canberra 2024 videos: Talks from the BSides Canberra 2024 security conference, which took place in September, are now available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how the opportunities for hackers have changed and how that has altered the pipelines that turn kids into criminals.
In this podcast, Tom Uren and Adam Boileau talk about the continued importance of hack and leak operations. They didn't really affect the recent US presidential election, but they are still a powerful tool for vested interests to influence public policy.

