Risky Bulletin Newsletter
November 27, 2024
Risky Biz News: Banshee Stealer shuts down after source code leak
Written by

News Editor
This newsletter is brought to you by Stairwell. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:
The developers of Banshee Stealer, an infostealer that targets macOS systems, have shut down their operation after an unidentified individual leaked their malware's source code online.
The incident took place earlier this week and was announced via hacking forums and Telegram channels.
The Banshee group launched its operation in August and is one of several macOS infostealers that were released this year.
According to an Elastic report, it can do all the things infostealers do, such as dump and steal passwords from browsers, steal crypto-wallet keys, collect OS data, and even run a phishing page once in a while.
However, its most memorable feature was its insanely high rental price of over $3,000 per month, which was about ten times more than what most infostealer gangs regularly charge for their products.
Let's just say the leak looks like an unsatisfied customer. This is quite common in hacking forums, where former customers often leak their seller's malware if they feel misled or just want to sabotage a rival.
Risky Business Podcasts
Risky Business is now on YouTube with video versions of our main podcasts. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Luxembourg DDoS attacks: The Luxembourg government has confirmed that a DDoS attack last month took out government sites and its emergency 112 services. [Additional coverage in RTL]
Blue Yonder ransomware attack: A ransomware attack on an Arizona IT company that makes software to manage supply chains is impacting the activities of some of the world's largest retailers. The attack impacted Blue Yonder, which boasts to serve over 3,000 companies. Companies like Sainsbury's and Morrisons in the UK and Starbucks in the US said the incident impacted their operations. The Blue Yonder attack took place on Thursday last week, and no ransomware gang has yet to take credit. [Additional coverage in SecurityWeek]
Vossko ransomware attack: A ransomware attack has temporarily stopped production lines at Vossko, one of Germany's leading frozen food producers. The company restarted activity over the past weekend after spending ten days recovering from the attack. No ransomware gang has taken credit for the attack, and it's unclear if the company paid the attackers. [Additional coverage in the Westfälische Nachrichten] [h/t Manuel Atug]
Geico fined over security breach: The state of New York has fined auto insurance company Geico $9.75 million for a 2020 security breach that exposed customer data. Hackers accessed Geico's online quoting tool and the personal data of millions of users, including 120,000 New Yorkers. The stolen data was later used to file fraudulent unemployment claims during the COVID-19 pandemic. Besides Geico, New York officials also fined auto insurer Travelers $1.55 million for a similar security breach. As part of the settlement, the two companies have also agreed to set up cybersecurity programs, deploy reasonable authentication procedures, and logging and monitoring systems.
LifeLabs breach report goes live after four years: The Canadian government has won a legal battle and has finally been allowed to publish a report on the 2019 breach of medical testing company LifeLabs. The company has sought to block the report's publication since 2020, citing "solicitor-client privilege." The now-public government report [PDF] found that LifeLabs "failed to take reasonable steps" to protect its patients' personal information and health data. The company is currently facing a major class-action lawsuit over the breach. More than 900,000 Canadians have filed claims in the lawsuit. [Additional coverage in the Vancouver Sun]
General tech and privacy
Firefox 133: Mozilla has released Firefox 133. New features and security fixes are included. The biggest feature in this release is a new anti-tracking feature, Bounce Tracking Protection, which is now available in Enhanced Tracking Protection's "Strict" mode.
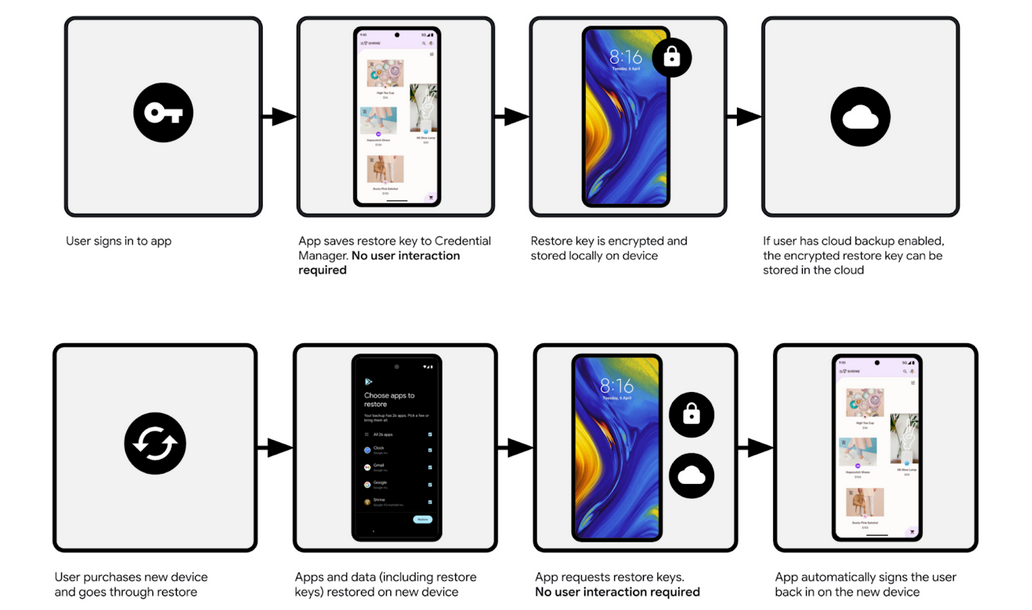
Android Restore Credentials: Google has developed a new feature for the Android operating system that will restore credentials and automatically log users back into apps after migrating to a new device. The new Restore Credentials feature will work by encrypting and syncing credentials to a cloud backup from where they can be restored during a future migration. Google says the feature is safe and works using Android's native backup and restore mechanism.
JavaScript trademark dispute: A group of major JavaScript and npm developers are preparing to mount a legal challenge to have Oracle's trademark over the term JavaScript annulled, claiming that the term is a shared public good and Oracle used fraudulent evidence to the USPTO back in 2019 when it renewed its trademark.
Cloudflare loses customer logs: Cloudflare says an incident on November 14 caused the company to lose heaps of customer logs.
"During the roughly 3.5 hours that these services were impacted, about 55% of the logs we normally send to customers were not sent and were lost."
FTC calls out smart device makers: An FTC investigation has found that 89% of 189 tested smart products are failing to inform users for how long the vendor plans to provide software updates. The agency says the practice leaves consumers in the dark if and for how long devices are supported.
Threads changes algorithm: Following BlueSky's meteoric rise in popularity, Meta has finally given in and will add a "Following" feed to its Threads platform. Until now, Meta decided what content you saw, regardless of who you followed. In the meantime, BlueSky has passed 20 million registered users, has been the most popular social media app on app stores for the past week, and its sudden rise has made the EU inquire about an EU office and the app's total number of EU users. According to Whipling, BlueSky's sudden rise has also made Chinese propaganda channels mad/sad after they spent years building their influence networks on Twitter.
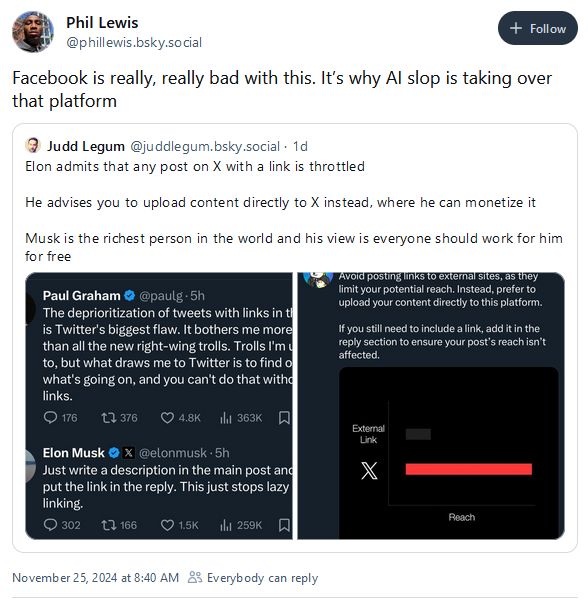
Musk admits throttling Twitter content: Elon Musk has confirmed that Twitter has been throttling and deprioritizing tweets that contain links to third-party websites.
Government, politics, and policy
Australia passes Cyber Security Act: The Australian government passed the Cyber Security Act on Monday. The Act will require certain businesses to report ransomware payments to the government and create a Cyber Incident Review Board to conduct no-fault, post-incident reviews of significant cyber security incidents. It will also empower the government mandatory cybersecurity standards and allow Australian cyber and intelligence agencies to share data more easily during cybersecurity incidents. [Additional coverage in the Australian Cyber Security Magazine]
Romania plans to ask the EU to investigate TikTok: The Romanian government plans to ask the EU to start an official inquiry into TikTok and its opaque algorithms after a pro-Kremlin extreme right candidate won the first round of the country's presidential election boosted by a campaign primarily hosted on TikTok. Officials claim the candidate came out of nowhere over the past month and got a massive boost on TikTok to the detriment of other candidates. Government officials say the social network had a massive impact on its elections and have asked the EU to investigate TikTok's risk to EU democracies and fair elections. [Additional coverage in HotNews]
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Mike Wiacek, CEO and founder of Stairwell, about the occasionally dysfunctional relationship between IT and security teams. Mike talks about how security vendors need to reach out to turn IT teams into allies.

Arrests, cybercrime, and threat intel
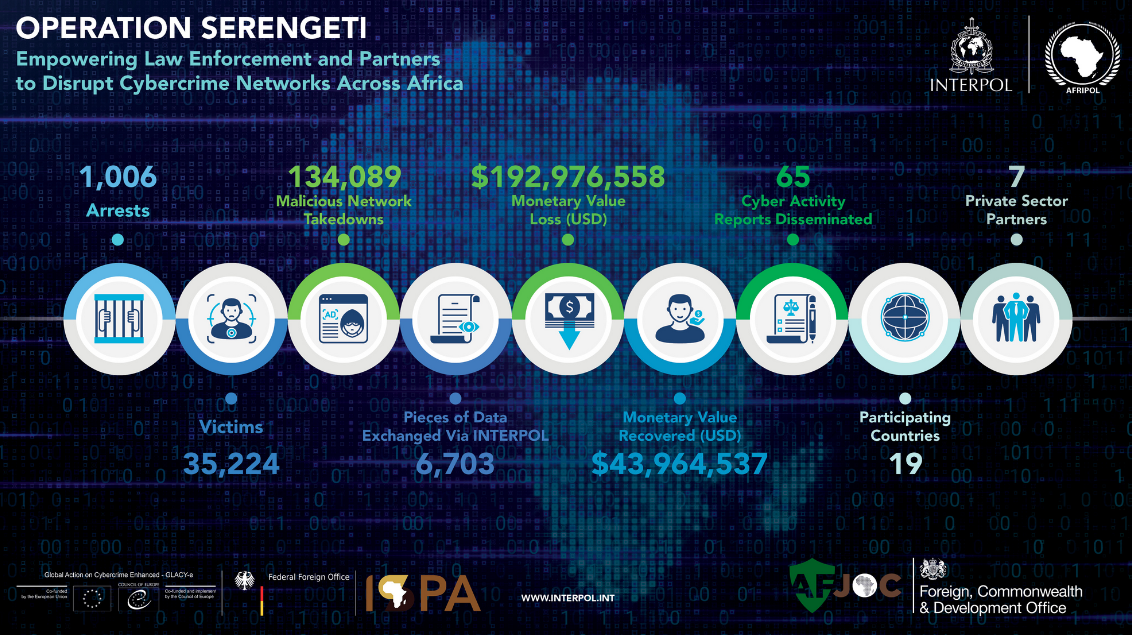
Operation Serengeti: Law enforcement agencies from 19 African countries have arrested over 1,000 suspects involved in cybercrime operations. The suspects were allegedly involved with ransomware, BEC, digital extortion, and online scams. The arrests took place as part of Interpol's Operation Serengeti. Earlier this month, Interpol also took down over 1,000 servers used for illegal cyber activities.
Hacker charged in Missouri: US authorities have charged a Kansas City man for hacking into the computer systems at a nonprofit and a health club business. Officials say Nicholas Michael Kloster hacked the two companies and then offered to help them recover from the attack.
Everest negotiator trial: The trial of Florent Curtet is underway in France. He is accused of serving as a negotiator for the Everest ransomware gang. [h/t Gabriel Thierry]
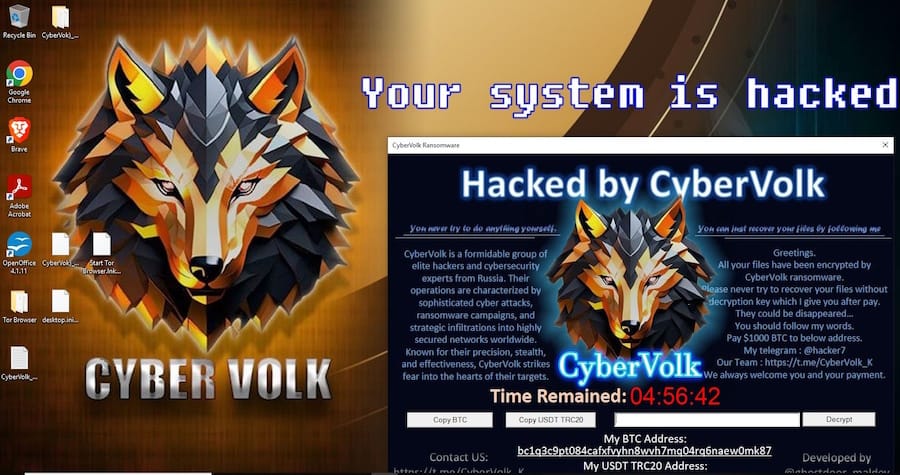
Indian hacktivists supporting the Kremlin: A new hacktivist group named CyberVolk emerged in May this year and has declared allegiance is launching cyberattacks in support of the Kremlin regime. According to SentinelOne, Rapid7, and ThreatMon, the group originated and appears to be based out of India. Initial CyberVolk operations included DDoS attacks, but the group has now also launched a Ransomware-as-a-Service portal in June this year. The ransomware appears to have been cobbled together using code from several leaked ransomware families. Recently, the group started to advertise their own webshell and infostealer. CyberVolk was banned from Telegram this month as part of the company's mass ban of hacktivist groups.
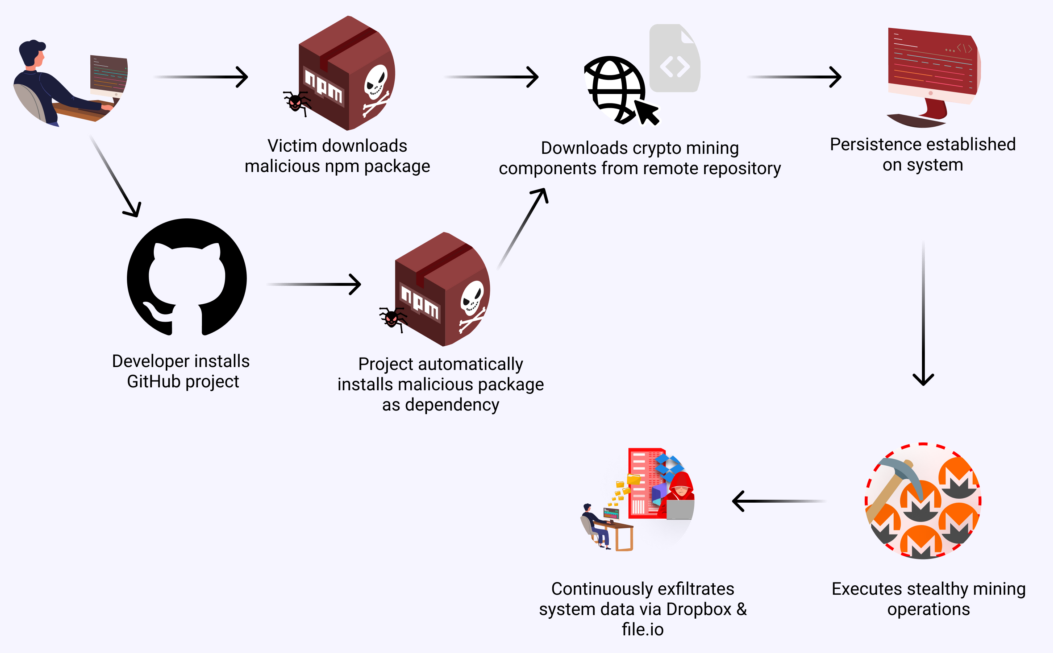
Malware survives on npm for almost a year: A malicious JavaScript library survived almost a year undetected on the official npm portal. Checkmarx says the package posed as an XML-RPC implementation that secretly stole SSH keys and other sensitive details. The malware also mined cryptocurrency on the infected systems. This is the second long-term supply chain attack discovered this month after Kaspersky also discovered a similar PyPI package that went undetected for a year as well.
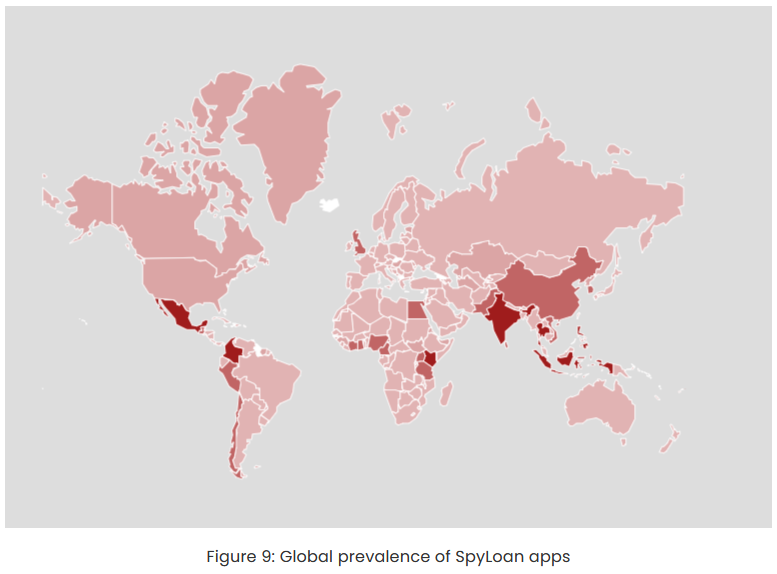
Malicious loan apps: McAfee has a deep dive into malicious loan apps distributed via the Play Store that lend users money, spy on them, and then use their personal data to coerce and harass victims to pay back the loans at higher rates.
Rockstar 2FA PhaaS: Trustwave has published a report on Rockstar 2FA, a relatively unknown Phishing-as-a-Service platform. The platform appears to be an updated version of the DadSec/Phoenix phishing kit, which Microsoft previously linked to a group named Storm-1575.
0ktapus: Wiz takes a jab at looking into a bunch of phishing domains and pages used by 0ktapus, a group also known as Scattered Spider, and how they can be fingerprinted and detected.
Elijah profile: Crumb has published a video profile on Noah Michael Urban, known online as Elijah and Sosa, a member of the Scattered Spider group. Urban was detained earlier this year.
Malware technical reports
Matrix botnet: A new threat actor named Matrix has assembled a massive DDoS botnet over the past year. Cloud security firm Aqua says the group has built the botnet through brute-force attacks and by exploiting vulnerabilities in unpatched devices. The vast majority of compromised systems appear to be hosted on the IP ranges of major cloud service providers. Access to the Matrix DDoS botnet is sold online using a Telegram bot named Kraken Autobuy. Besides DDoS attacks, some of the Matrix bots have also been seen mining cryptocurrency.
XorBot botnet: Security firm NSFocus looks at an emerging IoT malware family named XorBot.
ElPaco ransomware: Kaspersky looks at a new ransomware strain named ElPaco, a variant of the Mimic ransomware. Also, check out CyFirma's report from last week.
Sponsor Section
Stairwell gives you the confidence to know if, when, and where malware has ever been on your systems. We take a data search approach to security: collecting, storing, and continuously reassessing every executable file and indicator of compromise — across all time, at planet scale.

APTs, cyber-espionage, and info-ops
Operation Undercut: Recorded Future has published a report on Operation Undercut, an influence operation carried out by Russian company Social Design Agency. As usual, the campaign sought to undermine support for Ukraine in Western countries, usually by hijacking branding from respected outlets.
"Leveraging AI-enhanced videos and impersonating reputable news sources, Operation Undercut disseminates disinformation targeting audiences across the US, Ukraine, and Europe. This operation, running in tandem with other campaigns like Doppelgänger, is designed to discredit Ukraine's leadership, question the effectiveness of Western aid, and stir socio-political tensions. The campaign also seeks to shape narratives around the 2024 US elections and geopolitical conflicts, such as the Israel-Gaza situation, to deepen divisions."
RomCom group behind recent Firefox, Windows zero-days: A Russian cyber-espionage group named RomCom is behind two recent Windows and Firefox zero-days patched in November and October this year. The group lured victims to malicious sites where they exploited a Firefox and then a Windows Task Scheduler zero-day to plant backdoors on its targets' systems. According to security firm ESET, the group targeted both espionage targets in Ukraine and Europe, but also companies for cybercrime purposes.
APT-C-60: Japan's CERT has published a report on APT-C-60, a suspected South Korean espionage group. The report looks at the group's targeting of Japanese organizations in August this year. [Later edit: now in English too]
Earth Kasha: Trend Micro looks at a recent campaign from Earth Kasha, a sub-group of the APT10 Chinese espionage gang.
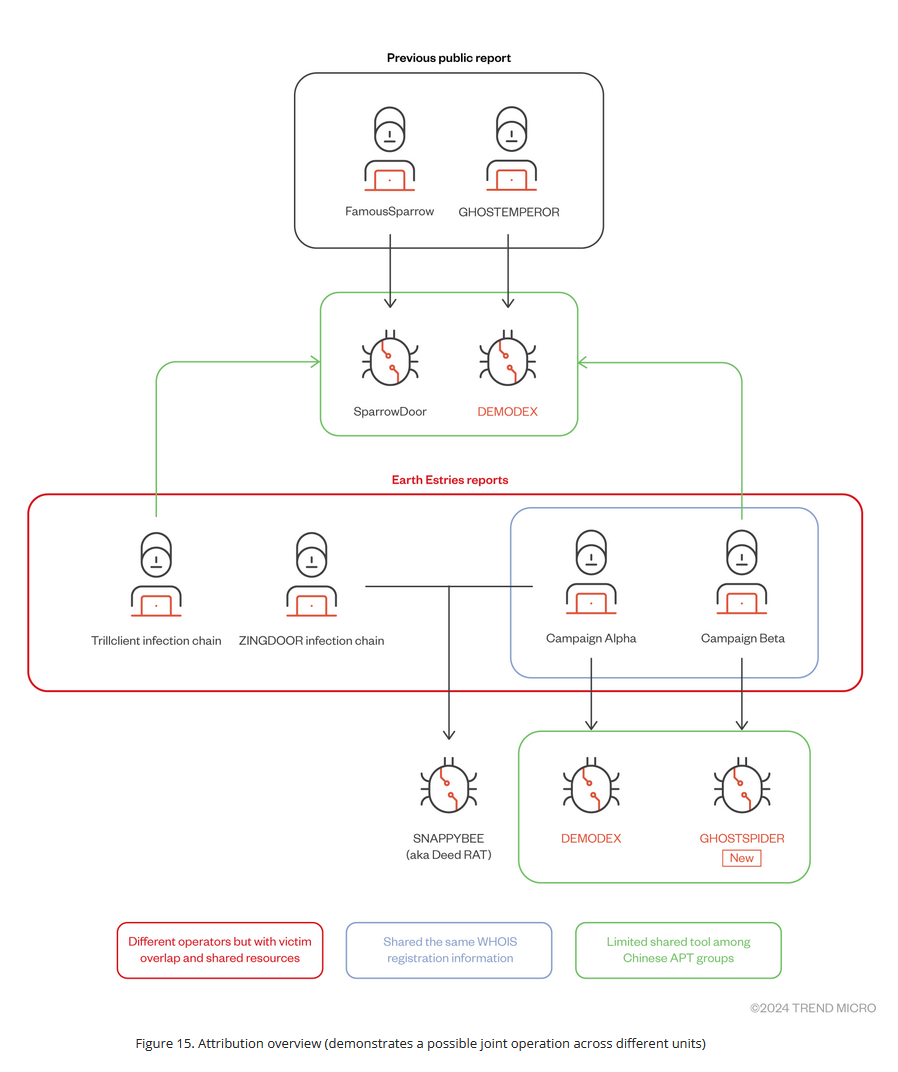
Earth Estries (Salt Typhoon): Trend Micro has published a profile on Earth Estries, the Chinese APT that recently hacked a bunch of US telcos and has made everyone lose their minds. The report covers past campaigns, their malware toolsets, and favorite tactics.
Vulnerabilities, security research, and bug bounty
ClipSp vulnerabilities: Cisco Talos has published write-ups for eight vulnerabilities they found in ClipSp, a Windows driver used to implement client licensing and system policies on Windows 10 and 11 systems.
Ruby deserialization attack update: Luke Jahnke, the researcher who developed the first Ruby deserialization RCE gadget, has updated his code to work with the language's upcoming v3.4 version.
PAN GlobalProtect RCE: AmberWolf researchers have recently presented details at security conferences on CVE-2024-5921, a new RCE in Palo Alto Networks GlobalProtect VPNs.
SonicWALL NetExtender RCE: The same team also presented details on CVE-2024-29014, an RCE in the SonicWALL NetExtender VPN client for Windows. Quite the busy bees!
Splunk security updates: Cisco has released two security updates for its Splunk SIEM platform.
GitLab security updates: GitLab has released patches for six vulnerabilities.
VMware security updates: And so has VMware for its Aria Operations platform.
IBM security updates: IBM has released this week patches for 20 vulnerabilities across several of its products.
Array Networks exploitation: CISA says threat actors are exploiting a 2023 vulnerability in the firmware of Array Networks' secure access gateways.
ProjectSend exploitation: Threat actors are exploiting a vulnerability in the ProjectSend file-sharing server. The attackers are targeting a vulnerability that was patched in May last year but was not assigned a CVE identifier due to an oversight. Security firm VulnCheck spotted the attacks after noticing over 200 ProjectSend servers with randomized characters for their login page title. The vulnerability exploited in the attacks has now received the CVE-2024-11680 identifier. VulnCheck says that based on Shodan data, only 1% of publicly exposed ProjectSend servers are running a patched version.
Infosec industry
Threat/trend reports: Howden, Kaspersky, Netcraft, and Proofpoint have recently published reports and summaries covering various infosec trends and industry threats.
Ekoparty 2024 videos: Talks from the Ekoparty 2024 security conference, which took place earlier this month, are available on YouTube. All the talks are in Spanish.
New tool—Awseye: Daniel Grzelak has released Awseye, a so-called Shodan for AWS, an OSINT and reconnaissance service that tracks and analyzes publicly accessible AWS data.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about different views on attribution and why it still matters for sophisticated state-backed groups.
In this podcast, Tom Uren and Patrick Gray talk about what the People's Liberation Army cyber operators have been up to. They used to be China's most visible cyber operators but have since disappeared.

