Risky Bulletin Newsletter
May 24, 2024
Risky Biz News: Backdoor found in court and jail AV recording software
Written by

News Editor
This newsletter is brought to you by Proofpoint. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

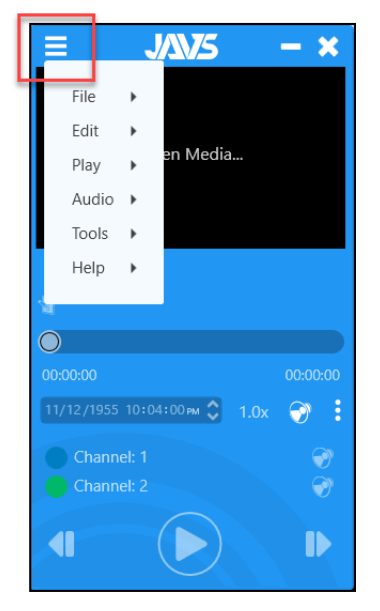
Cybersecurity researchers from Rapid7 and S2W have found a backdoor trojan inside a popular app used for recording courtroom and jury meetings.
The malware was found in the installer for JAVS Viewer, version 8.3.7, an app from Justice AV Solutions that allows customers to play back older recordings.
JAVS customers who downloaded the official installer from the company's website between April 1 and mid-May are likely infected with a version of the GateDoor backdoor.
The malware is written in Go and is the Windows version of RustDoor, a Rust-based backdoor that could infect macOS systems.
Previous reports from Bitdefender and S2W linked both versions of the malware to server infrastructure previously operated by the AlphV (BlackCat) ransomware operation.
Rapid7 has published information on its blog on how customers can determine if they installed the malicious version of the JAVS Viewer app—it drops a misspelled "fffmpeg.exe" encoder signed with a "Vanguard Tech Limited" certificate.
If systems are found to be infected, Rapid7 advises a full reimaging and the changing of all passwords stored on that system.
For its part, Justice AV Solutions appears to have been very responsive to the incident. Per a statement listed under Rapid7's report, the company says it removed the modified installer from its servers and is now conducting an audit of all JAVS software products.
The incident appears to be contained, but it's still unclear how the threat actor managed to put a backdoored file on its servers.
While Justice AV Solutions lists more than 10,000 customers on its website, it's likely that not all were impacted.
Breaches, hacks, and security incidents
Gala Games hack: The individual who exploited and stole $21 million worth of crypto tokens from the Gala Games platform has returned all the stolen assets. The hack took place earlier this week on Monday, when a hacker exploited the platform, minted $200 million worth of new tokens, and managed to steal $21 million before their access was cut off. The funds were returned after the company claimed it identified the hacker's identity and was working with law enforcement. Gala didn't specify if they are now dropping the case against the attacker. [Additional coverage in CoinTelegraph]
Change Healthcare hack: Members of the American Medical Association (AMA) have asked the US government to absolve them of HIPAA requirements related to Change Healthcare's February ransomware attack. AMA members have asked the US Department of Health and Human Services to hold Change Healthcare responsible for sending breach notifications related to the hack. Previously, Change Healthcare's parent company said it would handle breach notifications for some customers but not all. More than 100 healthcare organizations have signed an AMA letter [PDF] to the government. [Additional coverage in HealthcareDive]
NYSE hack fine: The US SEC has fined Intercontinental Exchange (ICE), the company behind the New York Stock Exchange (NYSE), $10 million for failing to report an April 2021 security breach in a timely manner.
pcTattletale leak: Stalkerware application pcTattletale is leaking screenshots captured from installed systems due to a vulnerability in its API. The issue was discovered by security researcher Eric Daigle, who reported the leak to the vendor earlier this month. Despite repeated contact attempts, the company has yet to respond to both the researcher and reporters. TechCrunch says the app is currently used by multiple hotels to keep an eye on employee systems. Screenshots taken by the app from hotel systems are now exposing the personal details of their guests.
Eindhoven leak: The Dutch city of Eindhoven has suffered a security breach and leaked the personal details of over 220,000 residents. [Additional coverage in Eindhovens Dagblad]
General tech and privacy
TLS Session Tickets and the GDPR: Polish privacy researcher Lukasz Olejnik has conducted a privacy audit of a TLS feature named Session Tickets that can allow TLS sessions to be easily resumed. The new feature is GDPR compliant, and Olejnik says that's a good thing since a privacy regulation impacting technical advancements may suggest "that something is very wrong with EU data protection law."
BlueSky gets DMs: The BlueSky social network now supports direct messages (DMs).
LastPass encrypts URLs: Password manager LastPass will start encrypting URLs stored in user vaults to protect user data against unauthorized access. LastPass is rolling out encrypted URLs after a major security breach in December 2022. A report claimed threat actors decrypted some of the stolen password vaults and then emptied cryptocurrency wallets with the recovered credentials. Encrypting URLs will prevent threat actors from linking credentials from a password vault to an online service. LastPass says it's encrypting URLs now because most devices have the memory to handle encryption algorithms.
DHS immigrants biometrics database: Experts from Georgetown University's law school say the DHS is misleading and intimidating immigrants to collect biometric and DNA profiles. Experts say that since 2020, the DHS has added more than 1.5 million DNA profiles to the national law enforcement database (CODIS), a 5,000% increase in just 3 years.
Edge gets screenshot protection: Microsoft has added new DLP security features to the enterprise version of its Edge web browser. New versions of Edge for Business will allow admins to restrict an employee's ability to take screenshots or capture the screen on sensitive pages. Administrators can also restrict users from printing Word, Excel, and PowerPoint documents marked as sensitive. The new features will be available in the coming weeks.
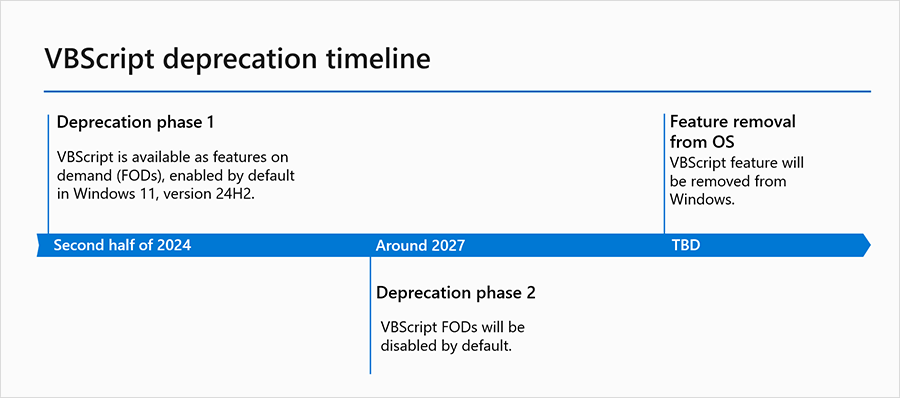
Microsoft's VBScript deprecation: Microsoft will deprecate and make VBScript a feature-on-demand (FOD) in the second half of the year with the release of Windows 11, version 24H2. VBScript will remain enabled by default, but administrators will now have the option to disable it if they wish to. VBScript will be disabled by default in 2027. Microsoft says it plans to remove VBScript from Windows but has not committed to an exact date yet.
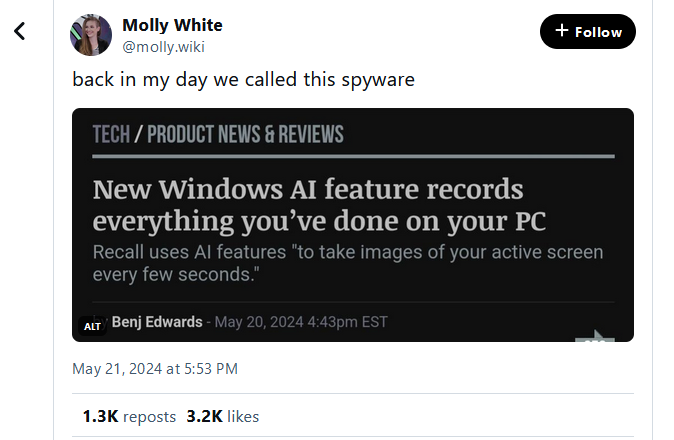
UK ICO to investigate Microsoft: The UK's privacy watchdog is investigating Microsoft over Recall, a new Windows 11 feature that takes screenshots of users' PCs every few seconds. Microsoft says the feature is intended to allow users to use a locally installed AI assistant to search through screenshots and a user's past activity. Recall is currently available on Microsoft's new select line of Copilot+ PCs. UK officials say they're looking into what safeguards Microsoft is putting in place to safeguard user privacy. Privacy and security experts have criticized Recall for exposing Windows users to new risks. Critics say the feature creates unredacted screenshots that may contain sensitive information, like passwords and bank numbers, and leave the data on the user's hard drive from where it can be stolen by malware.
Government, politics, and policy
Diverse Cybersecurity Workforce Act: Two Democrats from the US House of Representatives have introduced the Diverse Cybersecurity Workforce Act, a bill that would establish a program within CISA to promote the cybersecurity field to underrepresented and disadvantaged communities.
Goldstein replacement: CISA has nominated Jeff Greene to take over the position of the agency's Executive Assistant Director for Cybersecurity. Greene will replace Eric Goldstein, who will be leaving his post this month. Greene previously served in the White House's National Security Council's Cyber Directorate and as Director of US NIST. [Additional coverage in The Record]
EU anti-propaganda statement: Sixteen EU members have pledged to detect and fight propaganda and disinformation targeting the EU and neighboring countries. The 16 countries plan to share information, provide legal reactions, and even issue sanctions against foreign actors. They also plan to pressure online platforms to follow their legal obligations and crack down on disinformation campaigns. Countries that signed the statement include France, Germany, Poland, Austria, Bulgaria, Croatia, Czechia, Denmark, Greece, Italy, Latvia, Luxembourg, Portugal, Romania, Slovenia, and Spain. [h/t Lukasz Olejnik]
Deepfakes in the criminal code: The President of Latvia has asked the government to amend the country's criminal code to criminalize the creation of deepfakes for political use. The proposal suggests that offenders should face punishment of up to five years in jail. President Edgars Rinkēvičs' proposal comes after deepfakes were used in Slovakia's presidential and parliamentary election last year in support of an anti-EU and pro-Kremlin candidate. [Additional coverage in LSM]
Sponsor section
In this Risky Business News sponsor interview, Catalin Cimpanu talks with Proofpoint senior threat intelligence analyst Selena Larson about the latest changes in the threat actor landscape in the aftermath of several law enforcement takedowns and Microsoft tech stack changes.

Cybercrime and threat intel
BEC money launderer sentenced: US authorities have sentenced a Georgia man to 10 years in prison for laundering the proceeds of BEC and romance scams.
Novel phishing infrastructure: Huntress researchers have discovered the infrastructure of a phishing group that appears to combine several techniques for a novel form of phishing operations. Huntress says the threat actor appears to combine HTML smuggling, injected iframes, and session theft via transparent proxy—for a never-before-seen attack combo.
Elections, India, hacktivism, and cybercrime: Resecurity has published a report on how cybercrime and hacktivist groups are playing a role in this year's Indian elections, either through data dumps or influence operations.
Arc malvertising: Malwarebytes researchers look at a recent malvertising campaign using the new Arc browser as a lure to infect users with malware.
SMS scam abuse: Telecom security firm ENEA looks at how SMS scammers are abusing cloud services to host infrastructure without any issues from the hosters. YOLO!
PyPI macOS malware: DataDog researchers have spotted a cluster of malicious PyPI packages that target macOS users with malware.
Pegasus fakes: Indian security firm CloudSEK has published a report looking at all the recent ads published on the dark web and Telegram claiming to sell versions of the "Pegasus spyware"—obviously scams.
Storm-0539: Microsoft has published a more in-depth report [PDF] on Storm-0539, a threat actor that has been targeting the gift card departments at US retail corporations. Microsoft first spotted the group last December, and the group was recently at the center of an FBI security alert as well. [PDF]
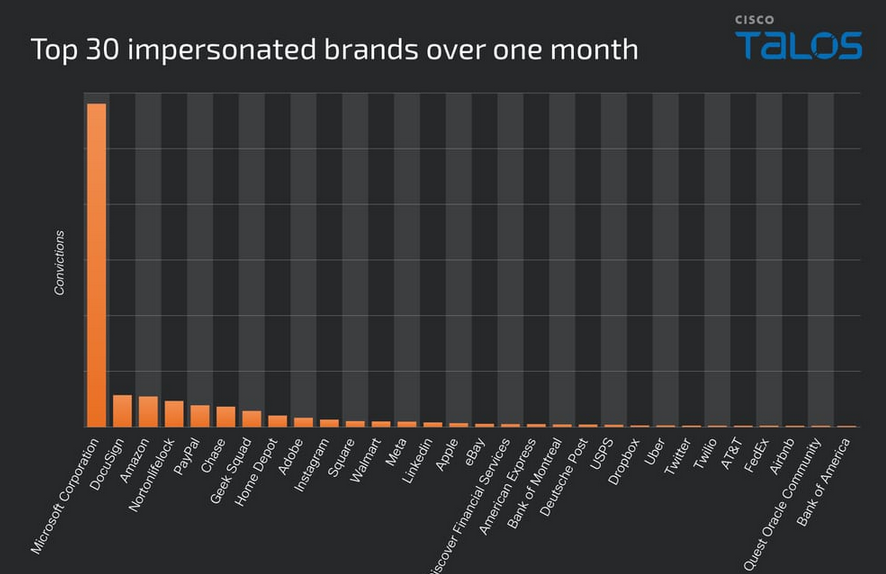
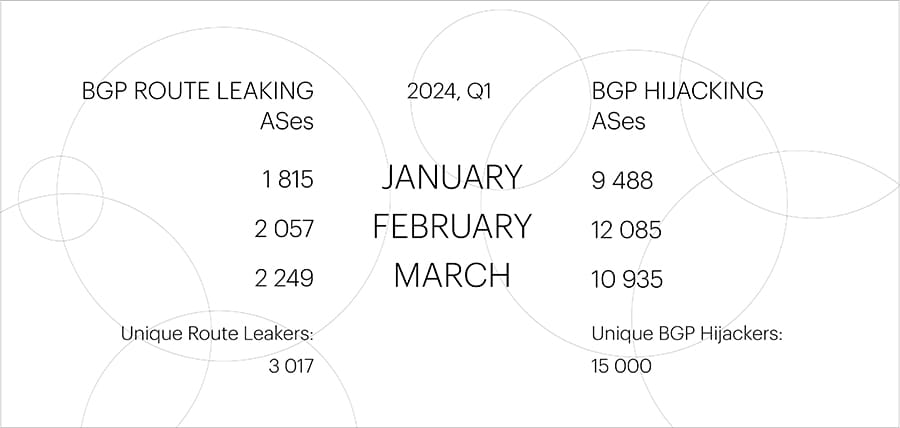
Threat/trend reports: Cisco Talos, Huntress, NCC Group, US NIST, and Qrator Labs have recently published reports covering infosec industry threats and trends.
Malware technical reports
Gootloader: Malwarebytes has published a technical deep dive at recent campaigns distributing the Gootloader malware family.
Iluria Stealer: CyFirma continues to find new malware advertised in underground cybercrime circles. Their latest finding is the new Iluria Stealer, an infostealer from the developer of the older Nikki Stealer.
New stealers: Kaspersky researchers look at three new infostealers they've spotted advertised online—Acrid, ScarletStealer, and Sys01. If nuclear war erupted tomorrow, the only things to survive would be cockroaches and infostealers.
ShrinkLocker ransomware: Kaspersky has discovered and documented a new ransomware strain named ShrinkLocker that used Windows' built-in BitLocker feature for data encryption.
CatDDoS botnets: Chinese security firm QiAnXin is seeing a surge in activity in IoT botnets using a variant of the Mirai malware named CatDDoS. The botnets have exploited over 80 vulnerabilities in different devices over the last three months to amass new bots and improve their attack capabilities. CatDDoS-related botnets are currently launching attacks on more than 300 targets on a daily basis. QiAnXin says it's seeing some of the botnets attempting to cannibalize each other's bots.
Sponsor Section
Proofpoint recently identified a SugarGh0st RAT campaign targeting organizations in the United States involved in artificial intelligence efforts, including those in academia, private industry, and government service. Proofpoint tracks the cluster responsible for this activity as UNK_SweetSpecter.

APTs, cyber-espionage, and info-ops
TikTok influence operations: TikTok says that in the first four months of the year, it disrupted 15 influence operations and removed 3,001 associated accounts. The company says most networks were trying to influence upcoming elections among a selected target audience. Most of the networks operated from the country they were trying to influence. Only two networks based out of China and Iran targeted audiences abroad, with pro-PRC and anti-US views, respectively. TikTok says the largest influence networks were found in Serbia, Indonesia, and Venezuela. A list of all networks and their goals is available here.
"For example, we disrupted a network targeting an Indonesian audience ahead of the country's presidential elections earlier this year, and another targeting the UK by artificially amplifying narratives about the UK's domestic political discourse."
SideWinder: Embee Research says it uncovered new SideWinder APT infrastructure by combining regex patterns, Whois records, and domain registrar data from past operations.
Transparent Tribe: IBM has published a report covering campaigns linked to Pakistan's Transparent Tribe APT that took place between late 2023 to April 2024. The campaign's targets included entities in India's government, defense, and aerospace sectors.
Kimsuky's Gomir: ShadowStackRE has published a breakdown of Gomir, a new Linux backdoor used by the Kimsuky APT.
Sharp Dragon expands: A suspected Chinese APT group named Sharp Dragon (Sharp Panda) has expanded its targeting to new regions, such as Africa and the Caribbean. The group has been active for years but has historically targeted only the Southeast Asia region. Security firm Check Point says the group is now using compromised accounts inside the governments of past victims to reach out to African and Caribbean governments and establish new footholds. Researchers say the group is careful when selecting new targets and uses publicly and readily available tools to blend in with the noise.
KeyPlug in Italy: Italian security firm YOROI takes a look at a few KeyPlug implants they found across Italy. KeyPlug is a backdoor used in the past by China's APT41.
Operation Diplomatic Specter: Palo Alto Networks says it's tracking a suspected Chinese APT conducting a campaign against diplomatic missions, embassies, and military targets across the Middle East, Africa, and Asia. Named Operation Diplomatic Specter, the campaign has been active since late 2022, and its main tools have been the TunnelSpecter and SweetSpecter backdoors.
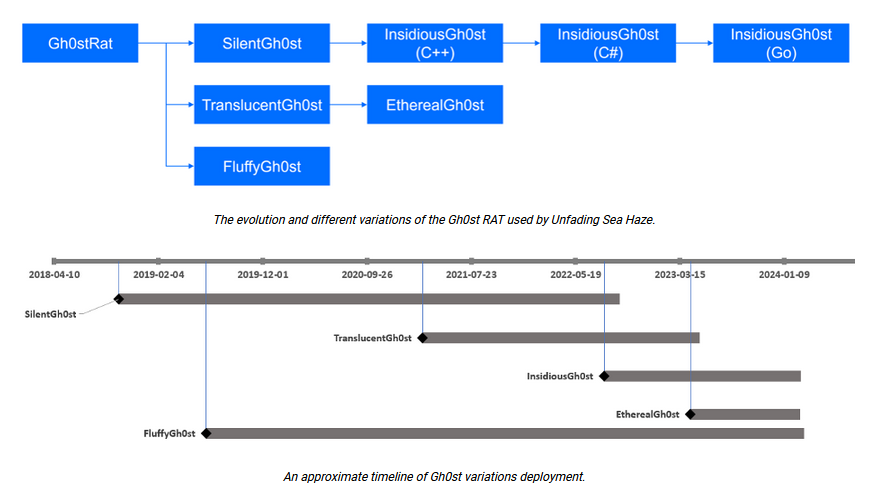
Unfading Sea Haze: A suspected Chinese APT named Unfading Sea Haze has gone under the radar for more than five years in attacks targeting countries around the South China Sea. Most of the attacks involved custom versions of the Gh0st open-source remote access trojan. Security firm Bitdefender says it discovered traces of the group's malware on the networks of eight military and government targets in the South China Sea region.
"The Unfading Sea Haze threat actor group has demonstrated a sophisticated approach to cyberattacks. Their custom malware arsenal, including the Gh0st RAT family and Ps2dllLoader, showcases a focus on flexibility and evasion techniques. The observed shift towards modularity, dynamic elements, and in-memory execution highlights their efforts to bypass traditional security measures. Attackers are constantly adapting their tactics, necessitating a layered security approach."
MSS front companies: Natto Thoughts looks at how the MSS appears to combine both front and real companies for its cyber contractor ecosystem.
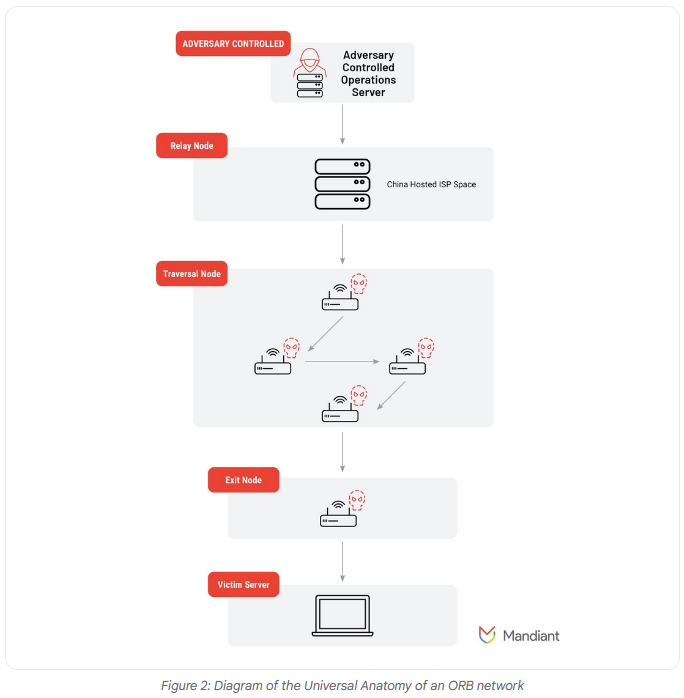
ORB usage: Google's Mandiant division warns about an increasing number of Chinese APT groups adopting ORB (operational relay box) networks to disguise their attack infrastructure. These networks are made up of a mixture of residential proxy networks, VPS servers, and hacked routers and IoT devices. Threat actors are using these networks to hide malicious operations such as vulnerability scanning, exploitation attempts, C2 traffic, and data exfiltration. Mandiant says it's tracking multiple ORB networks in the wild. The biggest are SPACEHOP and FLORAHOX, used by groups like APT5 and APT31, respectively.
Vulnerabilities, security research, and bug bounty
Apple's WPS is leaking: Apple's Wi-Fi Positioning System (WPS) is leaking too much information about nearby devices to a threat actor querying its official API. A team of academics says this data can be collected over time to create a map of WiFi-capable devices around the globe, even for non-Apple devices. Researchers say that by constantly updating this map, they can track the movement of individuals and groups of people over time. For example, researchers say they were able to accurately track the movement of Starlink terminals used by both Ukrainian and Russian forces in their recent conflict. They also tracked how Gaza residents slowly moved to the South of the Gaza Strip in the recent Israeli-Palestine conflict. [Additional coverage in KrebsOnSecurity/Research paper PDF]
Veeam auth bypass: Backup and recovery software maker Veeam has released security updates that fix five vulnerabilities, including an authentication bypass issues (CVE-2024-29849) in its enterprise backup solution. If you're a company that is a potential target of ransomware campaigns, you may want to patch this issue to prevent threat actors from deleting your backups and forcing you into a corner.
WinRAR bug write-up: Security researcher Siddharth Dushantha has published a write-up of a bug he found in WinRAR's Linux and Windows CLI clients.
PDF.js bug write-up: Codean's Thomas Rinsma has published a write-up of a bug he found in Mozilla's PDF.js PDF file viewer. The bug could have allowed threat actors to run malicious code inside apps where the PDF.js library was used and left misconfigured. It's a pretty niche scenario, but 10/10 on the nasty scale.
GitHub ES PoC: Proof of concept code is now available for that CVSSv3 10/10 auth bypass in GitHub enterprise servers (CVE-2024-4985).
Security audits: Boost and ExpressVPN have published security audits this week. The Boost audit found seven vulnerabilities, while the ExpressVPN audit looked at the company's no-logs policy.
Cisco security updates: Cisco has released seven security advisories for its products.
GitLab security updates: GitLab has published security updates to fix seven vulnerabilities, including a one-click account takeover XSS.
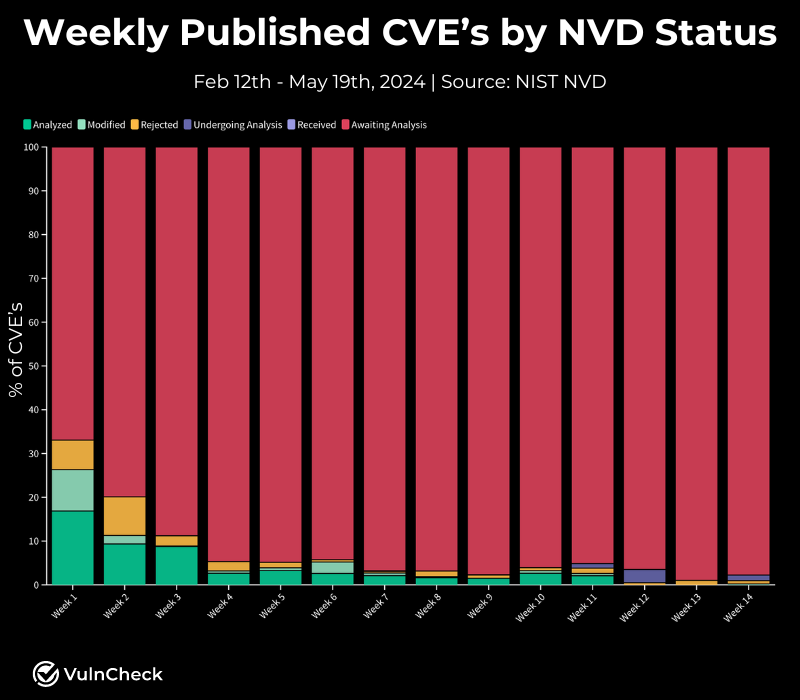
NVD backlog: More than three months after NIST stopped enriching the NVD database, the organization has yet to resume its normal activity. 93% of all vulnerabilities added to the NVD database over the last three months still lack crucial information. According to a report from security firm VulnCheck, NIST's involvement with the NVD is slowing down, with fewer vulnerabilities processed with each passing week.
Infosec industry
Kevin Mandia steps down: Mandiant CEO Kevin Mandia is stepping down from his role at the end of the month. The move comes after Google has finished integrating Mandiant into its cybersecurity teams. Google acquired Mandiant for $5.4 billion in late 2022, and the Mandiant threat intel team has been merged into Google Cloud. Mandia will transition into an advisory role at the company. [Additional coverage in CRN]
Tool update—Little Snitch: Objective Development has released v6 of the Little Snitch firewall app for macOS.
Risky Business Podcasts
In this edition of Between Three Nerds, Tom Uren and The Grugq talk to Elena Grossfeld about the strategic culture of Russian intelligence organizations.
