Risky Bulletin Newsletter
May 10, 2024
Risky Biz News: 68 tech companies pledge to CISA's Secure by Design project
Written by

News Editor
This newsletter is brought to you by Thinkst, the makers of the much-loved Thinkst Canary. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. On Apple Podcasts:

Sixty-eight of the world's largest tech companies have signed a voluntary pledge to design and release products with better built-in security features.
The pledge is part of CISA's Secure by Design (SbD) initiative, a project the agency started last year to promote better cybersecurity baselines and practices.
Signatories include the likes of Amazon, Google, Microsoft, HPE, Cloudflare, and Netgear. The full list is in the table below.
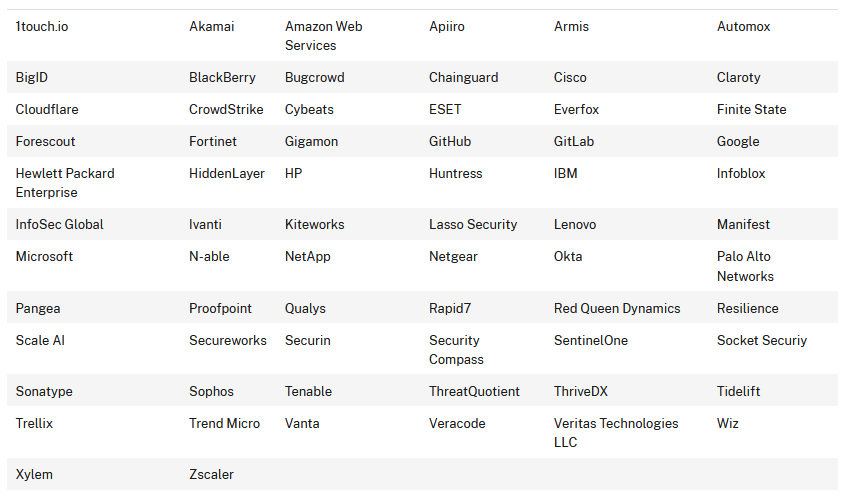
According to the pledge, the companies have committed to implementing a series of actions to improve the security of existing products and overhaul development practices to design products that have security built in from the start.
These practices and guidelines are the work of cyber-security agencies from the Five Eyes intelligence-sharing alliance. A summary is available via CISA [PDF], and the complete list of recommendations can be found via the UK NCSC [PDF].
In short, signatories have agreed to release products with better default passwords, to add MFA support, and to support a system for delivering security patches.
They also pledge to overhaul coding practices to avoid classes of vulnerabilities (e.g., SQLi, memory corruption, XSS, etc.) and to run vulnerability disclosure programs.
The full guideline addresses even more topics, such as geopolitics, supply chain, and pre and post-purchase considerations.
The pledge was announced this week at the RSA security conference in San Francisco.
Until this week, the SbD project was primarily known for releasing monthly advisories, asking developers to avoid coding software that contains certain classes of bugs. The new pledge takes CISA's SbD project to a new level of sophistication and is, by far, CISA's most ambitious project to date.
The project is CISA's non-regulatory approach to getting companies to improve the security of their products.
It is the agency's answer to a wave of cyberattacks that exploited vulnerabilities in poorly-coded products that allowed threat actors to breach government systems, carry out espionage operations, steal proprietary data, or deploy ransomware.
For the past two years, there have been discussions and criticisms that CISA should do more to address the issue of the software rot in the US government's networks.
Instead of a ham-fisted "I am the law" approach, CISA has been trying to get companies on board with hugs and cookies, allowing them to slowly overhaul internal procedures instead of having a parade of CEOs brought and shamed in front of Senate intel committees.
The informal pledge is good PR for both CISA and the signatories, to show both the White House and Congress that something is being done about a nagging issue.
Even if the results of this pledge will most likely take one or two years to show up for signatories, the documents released today provide a good step-by-step guide for any other tech company that may want to take a stab at that lucrative government contracting sector with their shiny new "Secure-by-Default" compliant products.
Breaches, hacks, and security incidents
European Parliament breach: A threat actor has hacked a recruitment platform used by the European Parliament. The hack took place in early 2024 and impacted around 8,000 individuals who applied for jobs through the European Parliament's PEOPLE platform. The platform was primarily used to hire temporary staff, such as interns, contract agents, or assistants. [Additional coverage in Euronews]
BC breach: The government of Canada's British Columbia province has suffered a security breach that impacted several of its IT networks. Officials have asked all government employees to change their passwords. Premier David Eby says the government is working with Canada's cybersecurity agency to investigate the hack and promised to provide additional details at a later date. [Additional coverage in Global News]
Dell breach: Tech giant Dell is sending emails and notifying customers of a security breach. The company says a threat actor gained access to one of its systems and stole customer data such as names, home addresses, and past acquisitions. Dell is disclosing the breach ten days after a threat actor began selling a batch containing the personal details of 49 million Dell customers.
DocGo breach: DocGo, a provider of mobile medical services, has disclosed a security breach in an SEC filing this week.
Zscaler denies breach: Security firm Zscaler has denied getting hacked after a threat actor claimed to sell access to its internal network on a hacking forum.
IB breach: The International Baccalaureate Organization (IBO) has disclosed a security breach. The organization says that some data from the 2018 school year was stolen.
Boeing 2023 ransomware incident: Airplane maker and defense contractor Boeing has confirmed that the LockBit ransomware gang had the audacity to request a whopping $200 million ransom following a breach of one of its systems in October of last year. The massive ransom demand was an urban myth in the ransomware world, but it's nice to see it confirmed. [Additional coverage in CyberScoop]
Ascension cyberattack: A cyberattack is disrupting healthcare services at hospitals and clinics across the US. The incident impacts healthcare provider Ascension, which operates 140 hospitals and 40 senior living facilities in 19 US states. The company is diverting new patients to other hospitals as it works to restore IT systems. Ascension says [archived] it's working with a security firm to investigate the incident. The company is one of the nation's leading nonprofit and Catholic health systems. [Additional coverage in CBS News]
1C Company cyberattack: Ukraine's military hackers claim to have carried out an attack against Russian enterprise software maker 1C Company. The attack crippled 1C's cloud platform and remote work services, crippling Russian companies downstream. This marks the fourth cyberattack claimed by Ukraine's Defence Intelligence Main Directorate (GUR) in the past month. [Additional coverage in Suspilne/English coverage in the Kyiv Independent]
Kosovo DDoS attacks: The government of Kosovo says Russian hackers are targeting its official websites with DDoS and defacement attacks. The attacks come after the country's leaders showed support for the Ukrainian government, its military, and accused Russian troops of genocide and war crimes. [Additional coverage in PrishtinaInsight]
Contec hijacks: A Chinese hacking group has hijacked more than 800 solar power generation monitoring devices across Japan. The incident took place at the start of May, and targeted devices made by Japanese company CONTEC. The hacked devices were used to conceal the hackers' identities and make illegal money transfers. [Additional coverage in Piyolog]
Balticom hack: Russian hackers hijacked Latvian TV station Balticom to broadcast the Kremlin;s May 9 Victory Day military parade. Balticom says the hack affected a content partner in Bulgaria, and that its core network was not breached. This is the second time in a month that Russian hackers hijacked Latvian TV, after a similar incident at TV station Tet in mid-April. [Additional coverage in LSM]
Russia's fake defacements: Russian hacker group Kilobyte V claimed to have hacked and defaced more than 100 Ukrainian websites and posted quotes delivered by Russian President Vladimir Putin on the Victory Day May 9 military parade. Most of the websites belonged to Ukrainian schools and universities. Unfortunately for Kilobyte V members, no evidence could be found about their "alleged" attacks. [Additional coverage in Kommersant]
WebDetetive/OwnSpy second hack: Hackers breached Brazilian spyware maker WebDetetive (OwnSpy) for the second time after a first hack in August of last year.
General tech and privacy
New tech slang, slop: Just like spam (canned meat) became the de-facto term for unwanted emails, "slop" is slowly becoming the term used to describe the AI-generated garbage slowly filling the internet.
StackOverflow AI drama: StackOverflow is banning users who are deleting past replies from their platform. The move comes after StackOverflow announced a partnership with OpenAI to harvest past replies for the benefit of StackOverflow's own wallet. Add StackOverflow to the slop category. [Additional coverage in Tom's Hardware]
Apple security: With the release of its M4-based devices, Apple has updated its Platform Security guide. [PDF]
Government, politics, and policy
Cybersecurity Posture of the US: The White House has published the first version of a new type of report named the Cybersecurity Posture of the US.
OAG privacy letter to Congress: Attorneys General from 16 US states have signed an open letter and asked Congress not to void and preempt state privacy laws as part of a new bill named the American Privacy Rights Act (APRA).
Nakasone move: Former CyberCom and NSA head has been named the founding director of the Institute for National Defense and Global Security, a new national security-focused hub at Vanderbilt University.
Sponsor section
In this Risky Business News sponsored interview, Tom Uren talks to Thinkst CTO Marco Slaveiro about staying current with modern attack trends and not falling for the trap of optimizing to catch red teams.

Cybercrime and threat intel
Skimmer gang detained: The US has charged seven men in connection with their alleged roles in a group that planted card skimmers at gas station pumps. All seven suspects are from Florida.
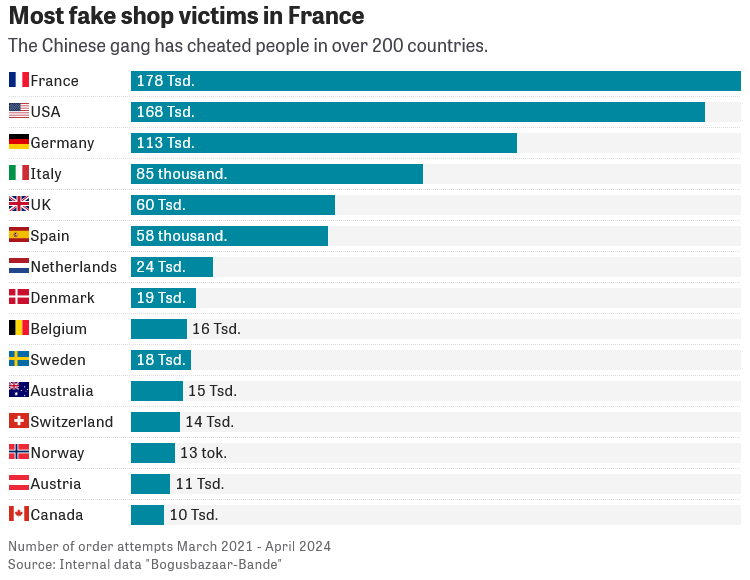
BogusBazaar: A Chinese criminal group named BogusBazaar is operating a network of more than 75,000 fake online stores designed to defraud customers. Over 850,000 customers have placed orders through the sites and lost funds or had their payment card details stolen. According to SR Labs, the vast majority of victims are from Western Europe and the USA. The security firm has released a portal named Fakeshop Finder [German] to help users see if an online store is part of the BogusBazaar network.
Scattered Spider returns: The Scattered Spider (aka 0ktapus, UNC3944, Roasted Oktapus, Scatter Swine, Octo Tempest, Muddled Libra) is still active and carrying out operations despite the recent arrests of some of its members. Security firm Resilience says it has seen the group mount new attacks against over 30 companies in the banking and insurance sector. The campaigns follow the group's old pattern of phishing and then SIM-swapping employees to take over their accounts.
Tycoon 2FA PhaaS: Proofpoint has published a report on Tycoon 2FA, a new phishing kit and Phishing-as-a-Service platform that launched in August of last year. A similar report is also available on the same service from Sekoia.
Cerberus (ex-Amnesia): Threat intel analyst g0njxa has published a profile of Cerberus. Formerly known as Amnesia, this is a traffer team known for working with infostealer gangs. The group is pretty popular and even had some songs made about them.
Cyber Army of Russia: WIRED has published a profile with Cyber Army of Russia, a pro-Kremlin faketivist group linked to the country's military.
Pro-Palestine/Hamas hacktivism: Radware has published a report on what is known as the "Cyber Price Tag," a pro-Palestine/Hamas DDoS campaign aimed at Western educational institutions.
NSO group lawsuit update: Israeli spyware vendor NSO Group has embarked on a campaign to discover how CitizenLab is tracking its tools. The company has filed several requests during the WhatsApp lawsuit legal proceedings to force CitizenLab to disclose its methodology. So far, NSO has filed two discovery orders, both of which have been shut down by the judge. [Additional coverage in The Intercept]
Threat/trend reports: Check Point, Kaspersky, and Sophos have recently published reports covering infosec industry threats and trends.
Malware technical reports
WordPress malware: The WPScan team has published a report on a JavaScript-based malware strain they're finding on WordPress sites. WPScan says the attacker is most likely exploiting sites that run older versions of the LiteSpeed Cache plugin. This campaign can be recognized by the same admin user planted on all hacked sites—wpsupp‑user.
AsyncRAT: McAfee looks at a malware distribution campaign that used common malspam techniques to deliver the AsyncRAT.
Viper: Hunt.io has published an analysis of Viper, an offensive security toolkit from China used by red teams and threat actors alike.
Mirai: Juniper Labs looks at a Mirai botnet variant targeting Ivanti Pulse Secure VPNs with two recently patched vulnerabilities.
Sponsor Section
This newsletter is brought to you by Thinkst, the makers of the much-loved Thinkst Canary.
We will be in SF for #RSAC next week. Pop by¹ for a demo, to grab a t-shirt, to see Canary in action, or just to talk detection that works.
— Thinkst Canary (@ThinkstCanary) April 29, 2024
It’s totally geeky, but we can’t wait 💪💚
__
¹ North Hall 6445
APTs, cyber-espionage, and info-ops
APT activity Q1 2024: Kaspersky has published its APT activity report for Q1 2024. Below are the main findings:
- The key highlights this quarter include Kimsuky’s use of the Golang-based backdoor Durian in a supply-chain attack in South Korea, and campaigns focused on the Middle East, including APTs such as Gelsemium, but also hacktivist attacks.
- The Spyrtacus malware used for targeting individuals in Italy demonstrates that threat actors continue to develop for multiple platforms, including mobile malware.
- APT campaigns continue to be very geographically dispersed. This quarter, we reported campaigns focused on Europe, the Americas, the Middle East, Asia and Africa.
- Geopolitics remains a key driver of APT development, and cyber-espionage remains a prime goal of APT campaigns.
- We also continue to see hacktivist campaigns: these have been centered mainly around the Israel-Hamas conflict, but not exclusively, as the activities of SiegedSec illustrate.
Emerald Divide: Recorded Future says that an Iranian influence operations group named Emerald Divide (Storm-1364) has been using the recent Israel-Hamas conflict to manipulate Israeli society and diminish trust in their own government. The group ramped up operations after the Hamas October 7 attack. Its recent campaigns have involved cybersecurity intrusions designed to collect personal data and then the doxing of Israeli public officials. Emerald Divide's influence network consists of more than 250 accounts spread out on seven different social media networks. Its primary activity takes place via Telegram, Twitter, and WhatsApp and often employs AI-generated content.
Russian APT activity: CERT-UA and SSSCIP have published their biannual report on Russian APT activity in Ukraine. The report covers H2 2023, and the main observation is that more and more Russian-based financially motivated threat actors are launching attacks on Ukrainian organizations, with access being most likely handed over to intelligence sources.
APT28: Russian cyberspies launched a spear-phishing campaign against the Polish government this week. Poland's cybersecurity agencies (CERT-PL and NASK) attributed the attacks to APT28, a Russian cyber-espionage group linked to the country's military intelligence unit. The campaign comes after Czechia, Germany, and Poland called out Russia's cyber-espionage operations in Europe.
Doppelganger and Havana Syndrome: Russian influence operations group Doppelganger has launched a wave of disinformation claiming the Havana Syndrome doesn't exist. The Doppelganger operation began days after American and German journalists linked the Havana Syndrome incidents to Russia's military intelligence agency. A joint 60 Minutes and Der Spiegel investigation linked the attacks to GRU Unit 2915, a Russian military intelligence unit specialized in assassinations and sabotage. [Additional coverage in The Insider]
Doppelganger and the campus protests: Besides that, the same Doppelganger group also got involved in the recent university campus protests. According to researchers, the group has set up fake versions of various legitimate news sites to push both pro-Palestine and pro-Israel disinformation. Per Recorded Future, these fake sites appear to be the work of a sub-group named CopyCop. [Additional coverage in Wired]
Vulnerabilities, security research, and bug bounty
New covert channel attack: A team of academics has found a way to extract and transmit data from air-gapped systems by using the cycle modulation (speed) feature of modern CPU processors.
FIDO2 bypass: Security firm Silverfort has published research on how a MitM attack can bypass FIDO2 authentication.
VMWare security updates: Broadcom has created four new portals for its security advisories.
Citrix PuTTY issue: Citrix has asked Citrix XenServer server owners to manually remove the PuTTY component to mitigate an issue (CVE-2024-31497) disclosed in April.
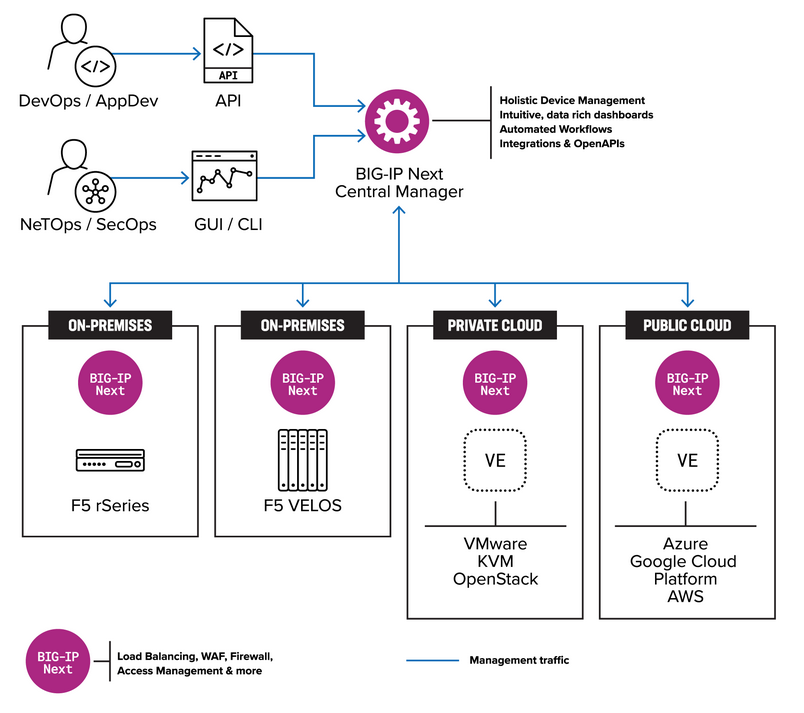
F5 security updates: Networking equipment maker F5 has released security updates for the month of May that fix 16 vulnerabilities in its products. The most critical ones are two bugs in F5's Next Central Manager, a platform for centralizing the management of an organization's F5 equipment. The bugs (CVE-2024-21793 & CVE-2024-26026) allow unauthenticated attackers to take control of the platform and then use it to pivot to other systems inside the organization's network. Both issues were discovered by security firm Eclypsium.
Infosec industry
Stupid names: Congratulations to CrowdStrike for naming a ransomware group PunkSpider, which is the same as a very well-known security tool.
New tool—PGDSAT: Software development company HexaCluster has open-sourced PGDSAT, a security assessment tool that checks around 70 security controls on PostgreSQL database servers.
New tool—Misconfig Mapper: Security firm Intigriti has open-sourced Misconfig Mapper, a tool to find, detect and resolve common security misconfigurations in various popular services, technologies and SaaS-based solutions. It supports the likes of Jira, Drupal, GitLab, Jenkins, Laravel, GraphQL, and others.
New tool—Parsnip: CISA has released Parsnip, a tool for parsing ICS protocols. The tool is based on Zeek.
New tool—CISA Vulnrichment: CISA has released a GitHub repo to enrich data on public CVEs. [Additional coverage in Axios]
New tool—CCTV: Security researcher Ivan Glinkin has developed a tool named CCTV (Close-Circuit Telegram Vision) that can track (some) Telegram users with a precision of 50 to 100 meters. [Additional coverage in 404 Media]
NetNoiseCon 2024: Talks from GreyNoise's NetNoiseCon 2024 security conference, which took place last month, are available on YouTube.
Risky Business Podcasts
In this edition of Between Two Nerds, Tom Uren and The Grugq look at how different types of secrecy-obsessed organizations learn.
